Accelerating APK Analysis with MCP-Driven JADX Workflows
Introduction
Reverse engineering Android applications typically requires switching between tools, searching through source code manually, and repeatedly opening files in a decompiler to trace how an application behaves. With the Model Context Protocol (MCP), this workflow can be streamlined. MCP allows local tools to expose structured data to an AI assistant such as Claude, enabling the AI to query source code, search patterns, and extract configuration details directly from a reverse-engineering environment. By integrating JADX with an MCP server, Claude can access decompiled APK content and respond to natural-language questions like “show exported activities,” “search for API keys,” or “open the AndroidManifest file,” which speeds up analysis and reduces repetitive manual steps.
Installation
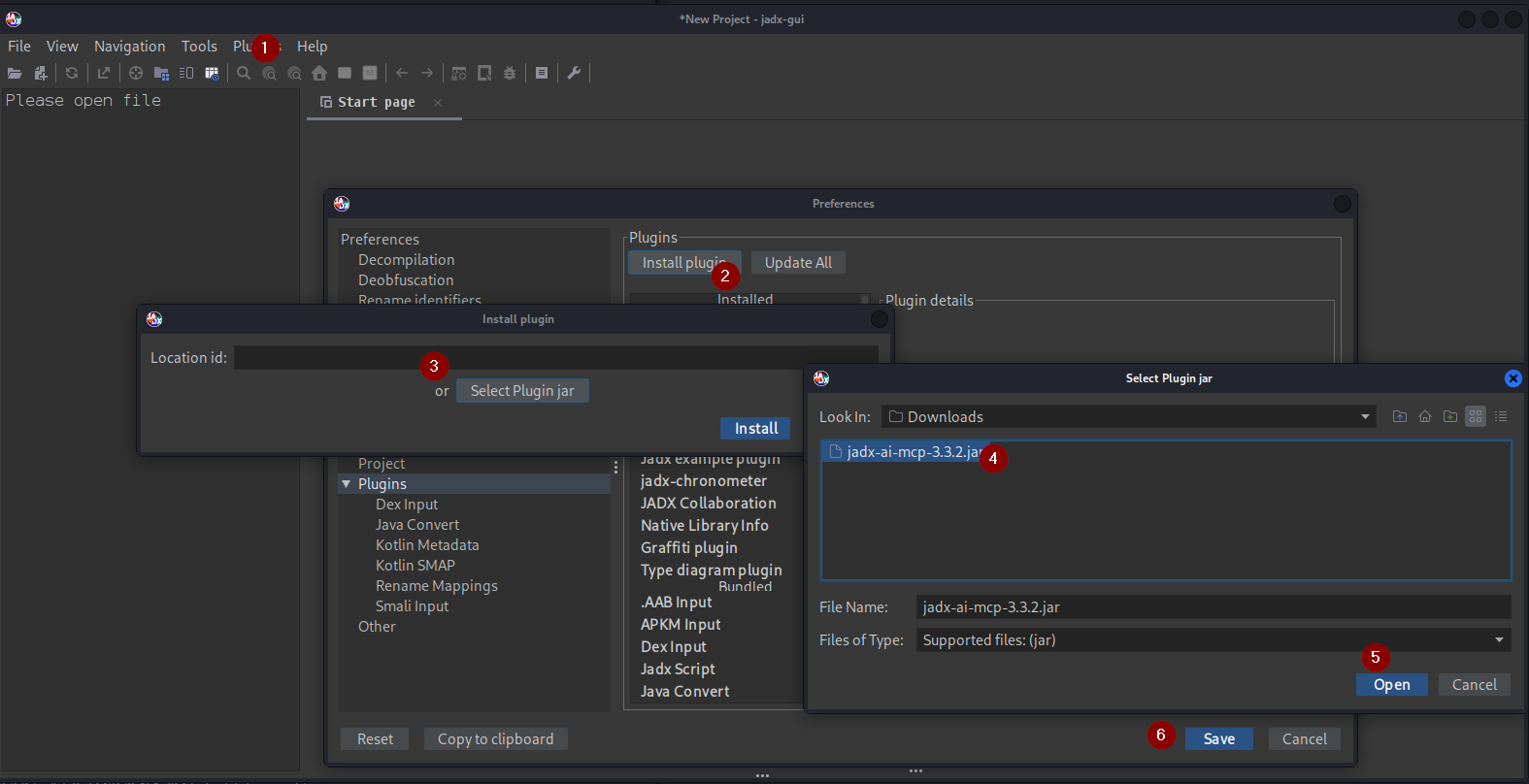
To install the MCP integration for JADX, begin by preparing your decompiled APK output using JADX as you normally would. Then download the two components from the jadx-ai-mcp GitHub repository: https://github.com/zinja-coder/jadx-ai-mcp the JADX MCP plugin (JAR file)1 and the MCP server package. Extract the MCP server files into a working directory on your machine, and create a Python virtual environment inside that folder. Once the environment is active, install the server dependencies using pip based on the provided requirements.txt. After the dependencies are installed, the MCP server will be ready to run locally through FastAPI and Uvicorn1
1
2
3
4
5
6
7
8
9
10
11
12
13
Navigate to jadx-mcp-server directory
cd jadx-mcp-server
# 4. This project uses uv - https://github.com/astral-sh/uv instead of pip for dependency management.
## a. Install uv (if you dont have it yet)
curl -LsSf https://astral.sh/uv/install.sh | sh
## b. OPTIONAL, if for any reasons, you get dependecy errors in jadx-mcp-server, Set up the environment
uv venv
source .venv/bin/activate # or .venv\Scripts\activate on Windows
## c. OPTIONAL Install dependencies
uv pip install httpx fastmcp
# The setup for jadx-ai-mcp and jadx_mcp_server is done.
(readmore for installation: https://github.com/zinja-coder/jadx-ai-mcp)1.
Next, install the MCP plugin into JADX so the decompiler can communicate with the server. You can do this automatically using the built-in jadx plugins –install command or by manually loading the downloaded JAR file through the Plugins menu in JADX GUI.
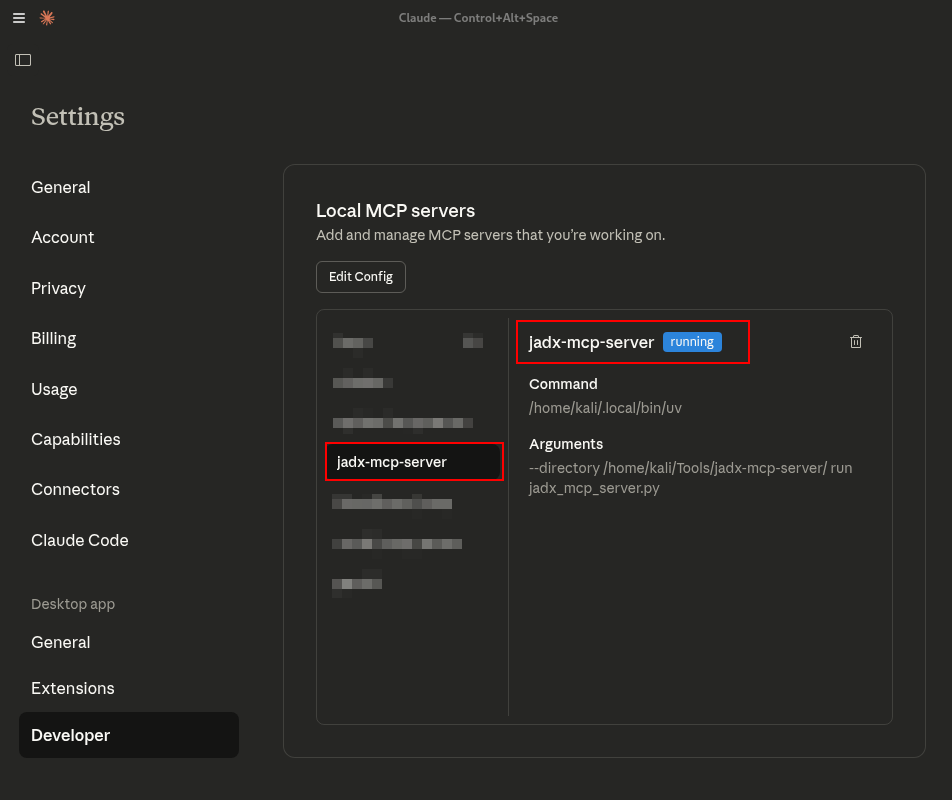
When the plugin is successfully installed, open Claude Desktop and add a new local MCP integration claude_desktop_config.json, pointing it to the same host and port used by the server. If the connection is successful, Claude will immediately detect the MCP server and display its available tools. At this point, the installation is complete and you can begin interacting with your decompiled APK through Claude (readmore for installation: https://github.com/zinja-coder/jadx-ai-mcp)1.
1
2
3
4
5
6
7
8
9
"jadx-mcp-server": {
"command": "/home/kali/.local/bin/uv",
"args": [
"--directory",
"/home/kali/Tools/jadx-mcp-server/",
"run",
"jadx_mcp_server.py"
]
}
Usage
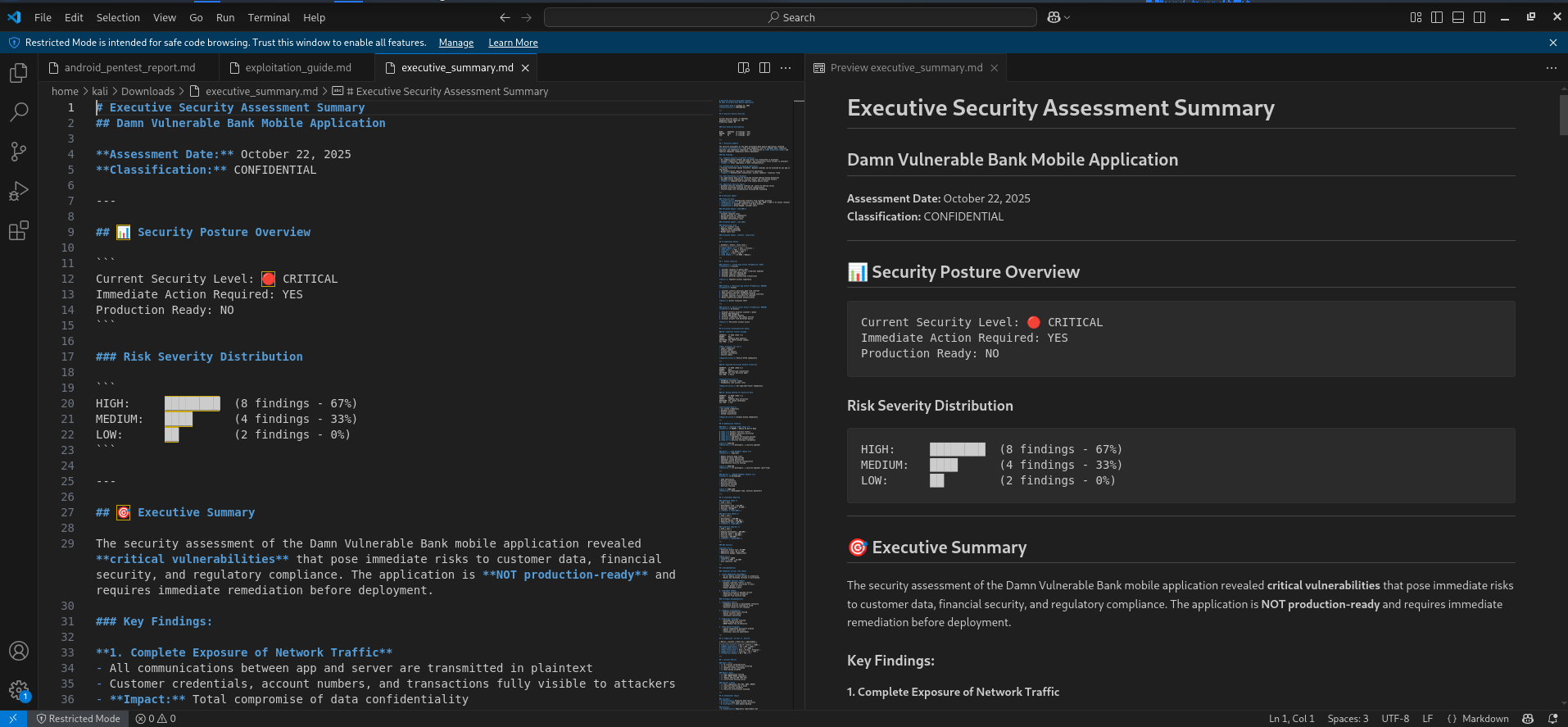
With the MCP server connected, you can now interact with JADX through Claude using natural conversation instead of constant manual navigation. For example, you can ask Claude to examine AndroidManifest.xml, locate sensitive API calls, search for hard-coded credentials, or explore the structure of a particular class. MCP allows Claude to request only the specific data it needs—rather than copying entire files into the prompt—making the interaction faster, cleaner, and more secure. This setup is especially useful when auditing an APK for vulnerabilities, understanding control flow, or documenting findings during research.
 Claude & Jadx MCP Server Usage (1)
Claude & Jadx MCP Server Usage (1)
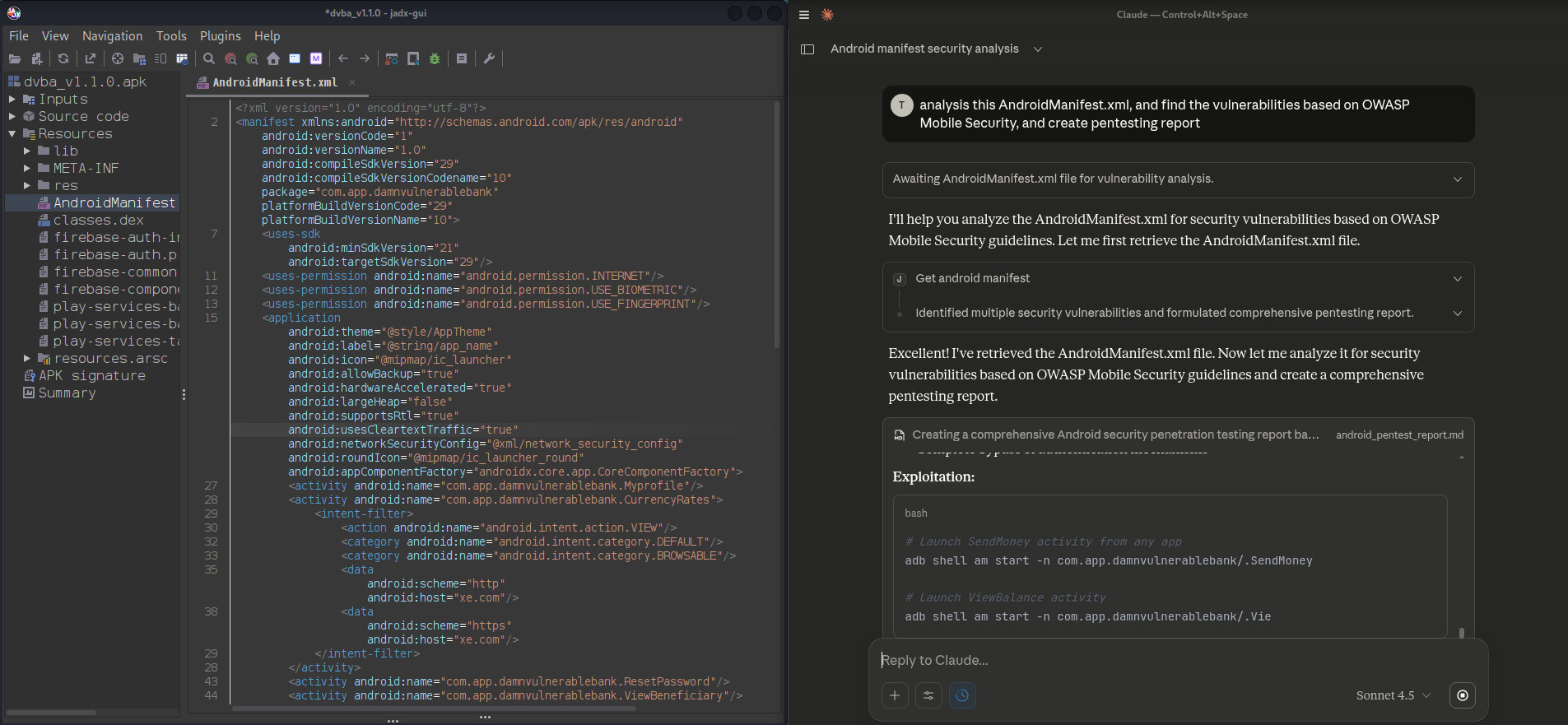
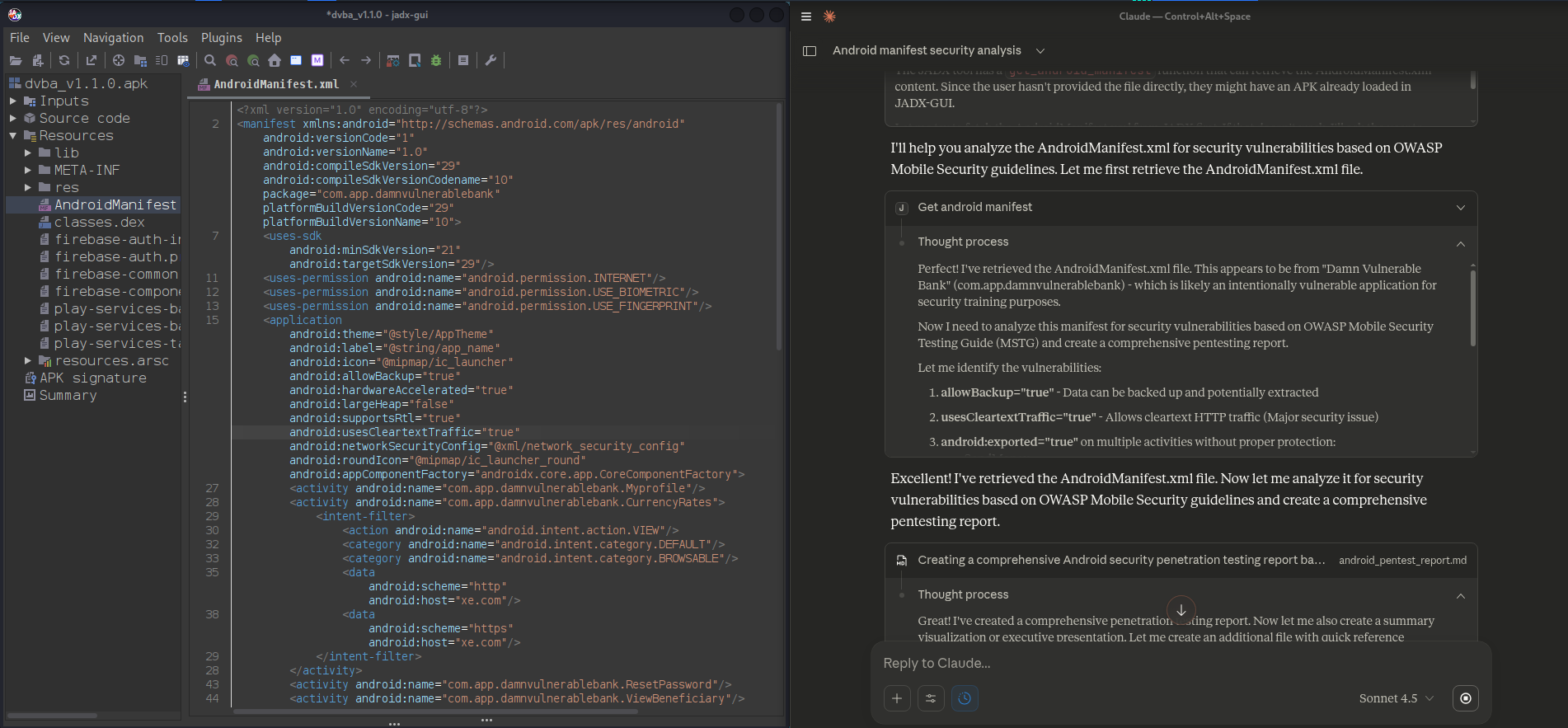 Claude & Jadx MCP Server Usage (2)
Claude & Jadx MCP Server Usage (2)
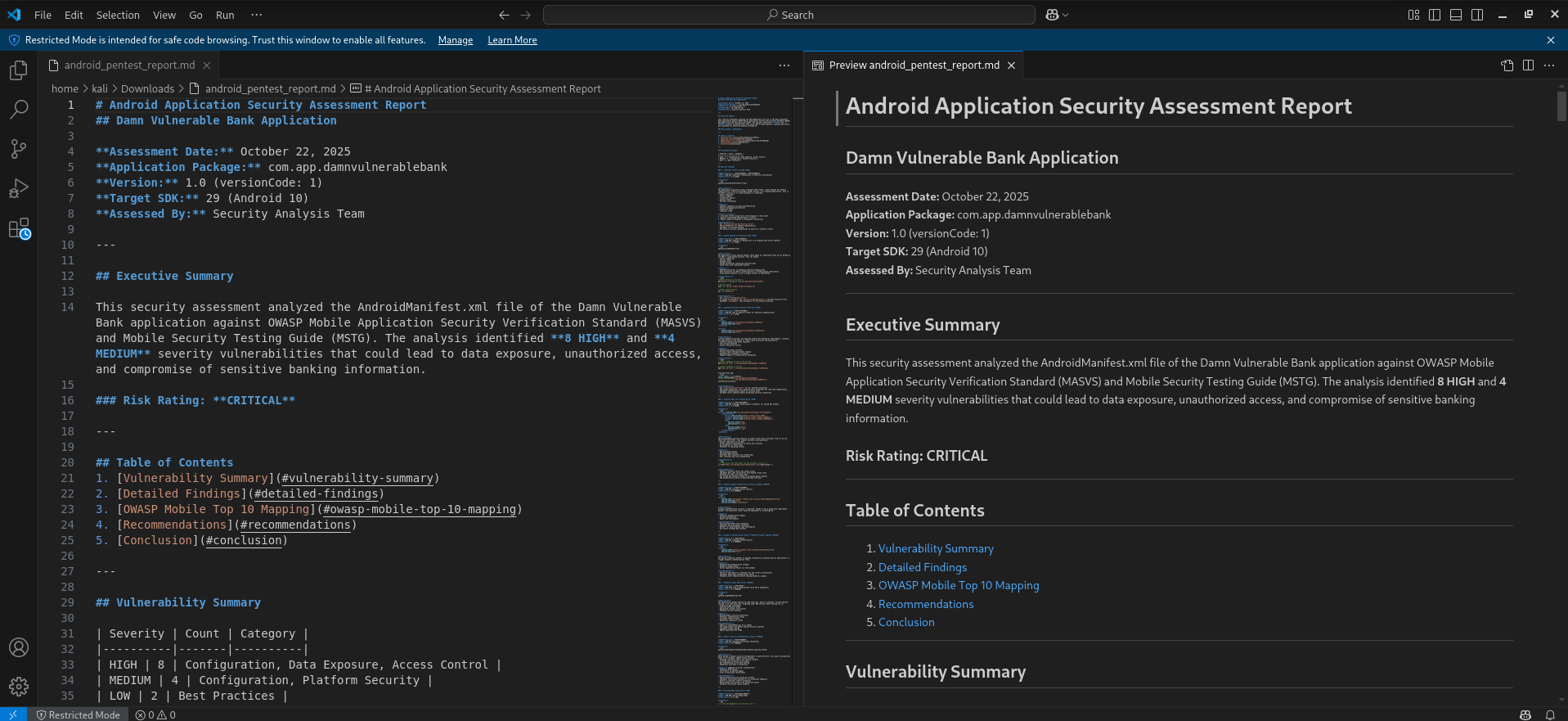
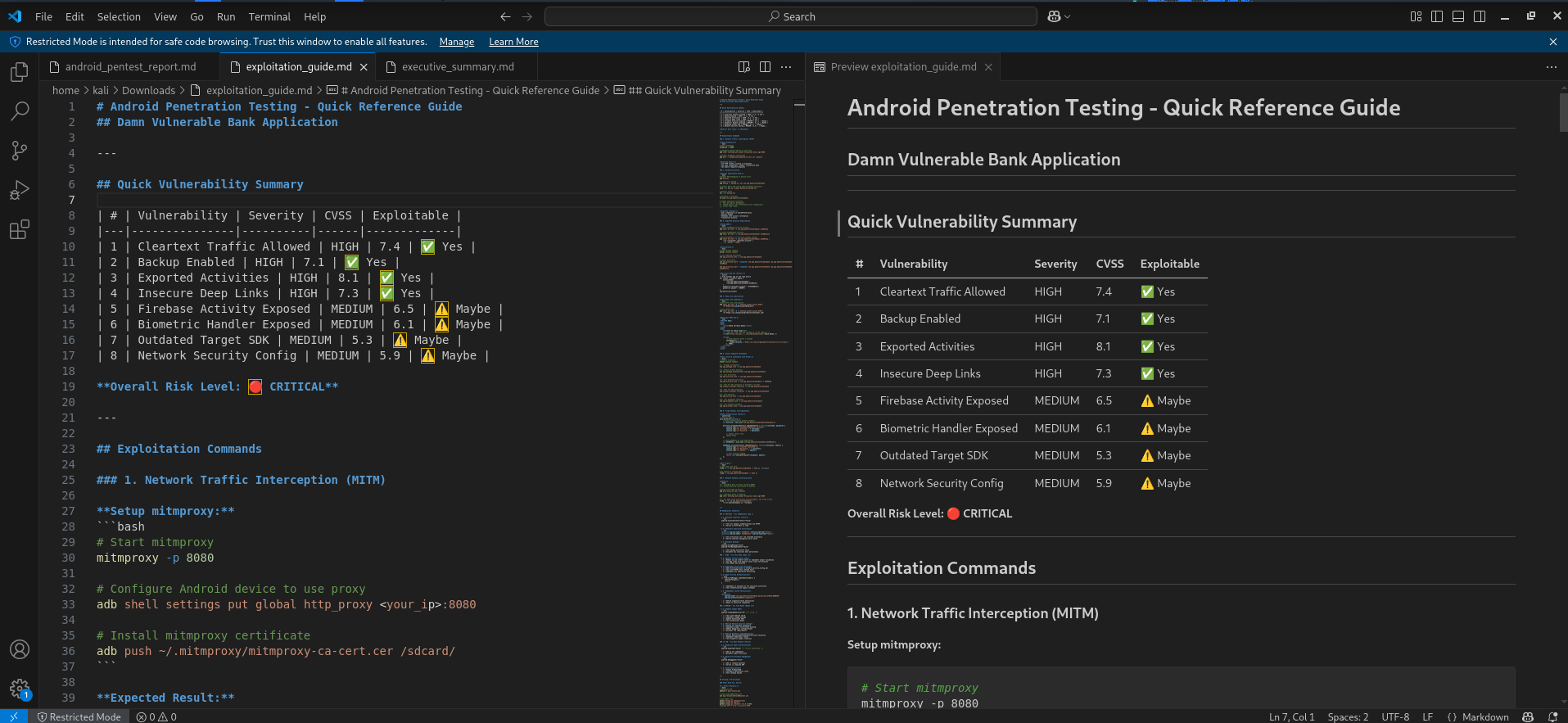
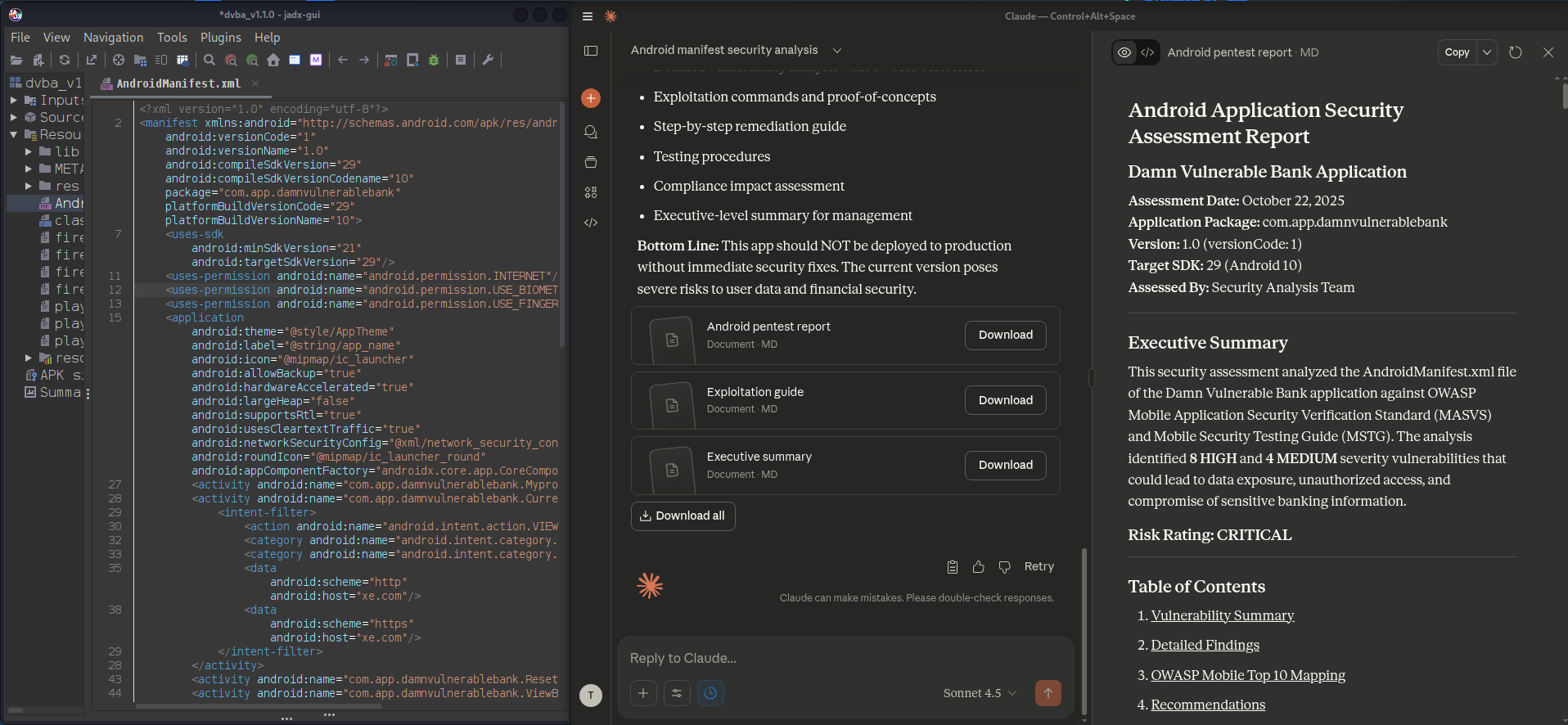 Claude & Jadx MCP Server Usage Created Vulnerability Report
Claude & Jadx MCP Server Usage Created Vulnerability Report
The result is a smoother workflow where the AI becomes a knowledgeable helper that can both fetch code and explain it in context.
Security Notes
Because the MCP server exposes local project data to an AI client, it should always be run in a controlled environment. Bind the server only to the local interface, avoid sharing the port externally, and restrict its access to the decompiled project folder so it cannot read unrelated files. If the APK contains sensitive or proprietary information, keep the entire workflow offline and prefer a local model environment or Claude Desktop rather than a cloud interaction. Treat the MCP server as you would treat any local debugging interface—powerful but requiring careful boundaries.
Conclusion
Combining JADX with an MCP server transforms reverse engineering into a more efficient, AI-assisted process. Instead of browsing files manually or running repetitive searches, you can let Claude handle the exploration and focus on interpreting results. This approach is easy to set up, stays fully under your control, and significantly accelerates analysis when working with Android applications. Whether you are auditing, researching, or studying APK internals, this workflow offers a faster and more intuitive way to understand application behavior.
Reference
-
“JADX-AI-MCP (Part of Zin MCP Suite)”- https://github.com/zinja-coder/jadx-ai-mcp ↩︎ ↩︎2 ↩︎3 ↩︎4